Creating a Domain Name¶
This section describes how to create a domain name and connect it to WAF. After connecting a domain name, WAF works as a reverse proxy between the client and server. The real IP address of the server is hidden and only the IP address of WAF is visible to web visitors.
Prerequisites¶
Login credentials have been obtained.
Domain Configuration Principle¶
Figure 1 shows how WAF works if the web server is using a proxy.
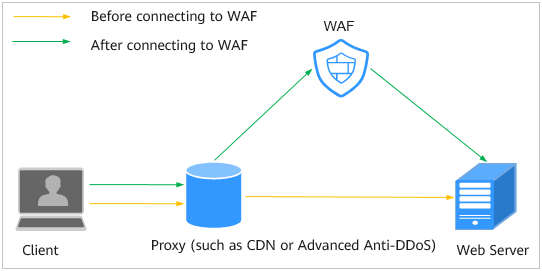
Figure 1 A proxy configured¶
DNS resolves the domain name to the IP address of a proxy (such as AAD) before your site is moved to WAF. In this case, the traffic passes through the proxy and then the proxy routes the traffic back to the origin server.
After your site is moved to WAF, DNS resolves your domain name to the access address of WAF. In this way, the proxy forwards the traffic to WAF. WAF then filters out illegitimate traffic and only routes legitimate traffic back to the origin server.
Change the back-to-source IP address of the proxy to the access address of WAF.
Add a WAF subdomain name and TXT record to the DNS records of your DNS provider.
Figure 2 shows how WAF works if the web server does not use a proxy.
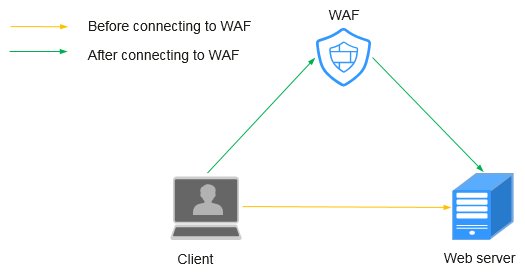
Figure 2 No proxy configured¶
DNS resolves your domain name to the origin server IP address before your site is connected to WAF. Therefore, web visitors can directly access the server.
After your website is connected to WAF, DNS resolves your domain name to the CNAME record of WAF. In this way, the traffic passes through WAF. WAF then filters out illegitimate traffic and only routes legitimate traffic back to the origin server.
Procedure¶
Log in to the management console.
Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project.Choose Security > Web Application Firewall.
In the navigation pane, choose Domains. Figure 3 shows an example.
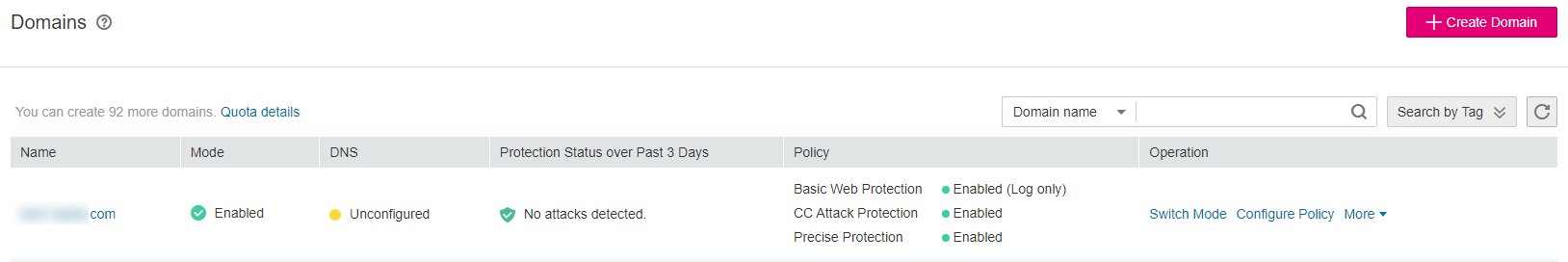
Figure 3 Domains¶
Note
In the upper part of the domain name list, click Quota details to view the domain name quota.
In the upper right corner of the domain name list, click Create Domain.
On the Create Domain page, specify required parameters by referring to Table 1. Figure 4 shows an example.
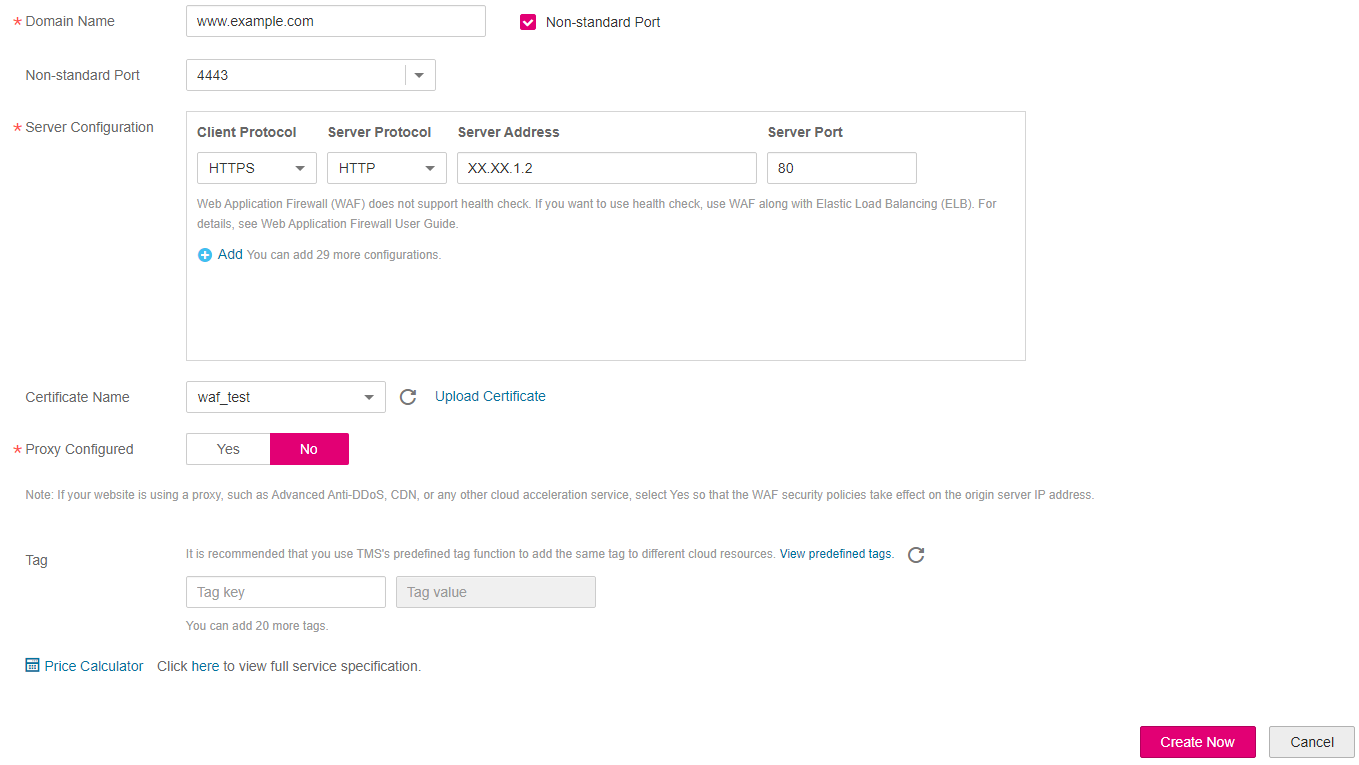
Figure 4 Configuring basic settings¶
Table 1 Parameter description¶ Parameter
Description
Example Value
Domain Name
A domain name to be protected, which can be a single domain name or a wildcard domain name.
Single domain name: For example, www.example.com
Wildcard domain name
If the server IP address of each subdomain name is the same, enter a wildcard domain name. For example, *.example.com.
If the server IP addresses of subdomain names are different, add subdomain names as single domain names one by one.
Single domain name: www.example.com
Wildcard domain name: *.example.com
Non-standard Port
Set this parameter only if Non-standard Port is selected.
If Client Protocol is HTTP, WAF protects the standard port 80 only by default. To protect a non-standard port, select Non-standard Port and then select a value from the Non-standard Port drop-down list.
If Client Protocol is HTTPS, WAF protects the standard port 443 by default. To protect a non-standard port, select Non-standard Port and then select a value from the Non-standard Port drop-down list.
For details about non-standard ports supported by WAF, see Web Application Firewall.
4443
Server Configuration
Address configurations of the web server, including Client Protocol, Server Protocol, Server Address, and Server Port.
Client Protocol: Type of client protocol. The options are HTTP and HTTPS.
Server Protocol: Protocol used by WAF to forward requests to the server. The options are HTTP and HTTPS.
Note
For details about configuring Client Protocol and Server Protocol, see Rules for Configuring Client Protocol and Server Protocol.
Server Address: IP address (generally the A record before the domain name is connected to WAF) or domain name (generally the CNAME before the domain name is connected to WAF) of the web server that a client accesses
Note
Web Application Firewall (WAF) does not support health check. If you want to use health check, use WAF along with Elastic Load Balancing (ELB). For details about how to configure ELB, see Backend Server (Enhanced Load Balancer). After ELB is configured, the elastic IP address (EIP) of ELB is used as the value of Server Address to connect to WAF for health check.
Server Port: Port number used by the web server
Client Protocol: HTTPS
Server Protocol: HTTP
Server Address: XXX.XXX.1.1
Server Port: 80
Certificate Name
If Client Protocol is HTTPS, select an existing certificate or upload a new certificate. For details about how to upload a new certificate, see Step 7.
None
Upload a new certificate if Client Protocol is HTTPS.
Click Upload Certificate. In the displayed Upload Certificate dialog box, enter the certificate name and paste the certificate file and private key to the corresponding text boxes. Figure 5 shows an example.
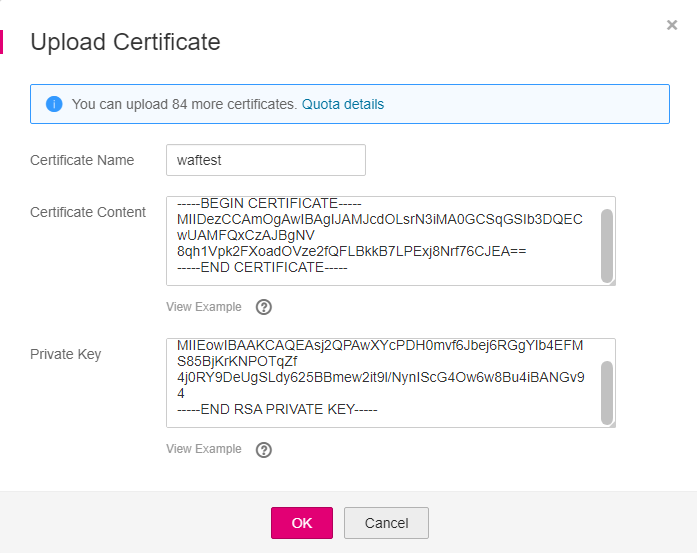
Figure 5 Uploading a certificate¶
Note
In the Upload Certificate dialog box, click Quota details to view the certificate quota.
WAF encrypts and saves the private key to keep it safe.
For details about the combination sequence of a certificate chain, see How Do I Fix an Incomplete Certificate Chain?
Currently, only .pem certificates are supported. If the certificate is not in .pem format, convert it into a .pem certificate by referring to Table 2 before uploading.
Table 2 Certificate conversion commands¶ Format
Usage (Using OpenSSL)
CER/CRT
Rename the cert.crt certificate file to cert.pem.
PFX
Obtain a private key. For example, run the following command to convert cert.pfx into cert.key:
openssl pkcs12 -in cert.pfx -nocerts -out cert.key -nodes
Obtain a certificate. For example, run the following command to convert cert.pfx into cert.pem:
openssl pkcs12 -in cert.pfx -nokeys -out cert.pem
P7B
Convert a certificate. For example, run the following command to convert cert.p7b into cert.cer:
openssl pkcs7 -print_certs -in cert.p7b -out cert.cer
Rename certificate file cert.cer to cert.pem.
DER
Obtain a private key. For example, run the following command to convert **privatekey.der** into privatekey.pem:
openssl rsa -inform DER -outform PEM -in privatekey.der -out privatekey.pem
Obtain a certificate. As an example, run the following command to convert cert.cer into cert.pem:
openssl x509 -inform der -in cert.cer -out cert.pem
Click OK.
Set Proxy Configured. The default value is No.
Important
The bypassed option is unavailable during proxy use.
If your website is using a proxy such as Advanced Anti-DDoS (AAD), Content Delivery Network (CDN), or any other cloud acceleration service, select Yes so that the WAF security policies take effect on the origin server IP address. If this parameter is No, WAF cannot obtain the real IP address requested by a web visitor.
Note
If a proxy such as CDN is used, WAF obtains the real source IP address of a client from the HTTP Header X-Forwarded-For by default. If the proxy does not use X-Forwarded-For to identify the real source IP address of a client, click
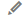 next to X-Forwarded-For in the row of Source IP Header. In the dialog box displayed, select an existing source IP header or select Custom and enter a source IP header.
next to X-Forwarded-For in the row of Source IP Header. In the dialog box displayed, select an existing source IP header or select Custom and enter a source IP header.If your website does not use a proxy, select No.
(Optional) Configure a tag.
You can select an existing tag key and tag value from the Tag key and Tag value drop-down lists or click View predefined tags to create a tag on the TMS console.
Click Create Now. In the upper right corner of the page, if Domain created successfully is displayed, the domain name is created.
Note
If you do not want to connect the domain name to WAF in this step, click Next. Then click Finish. DNS is displayed as Unconfigured. Later, you can refer to Connecting a Domain Name to finish domain connection.
If a proxy such as CDN or AAD is used, you need to configure the back-to-source IP address, subdomain name, and TXT record. Figure 6 shows an example.
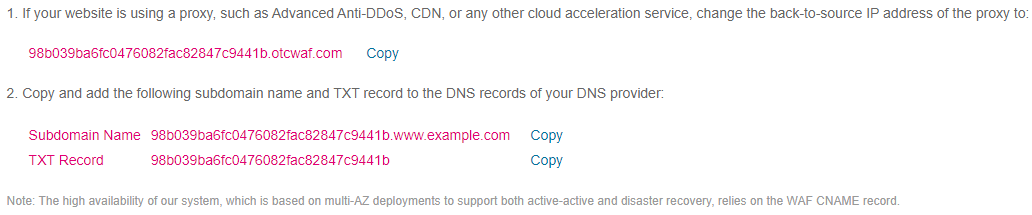
Figure 6 Connecting a domain name¶
Configure the back-to-source IP address of the proxy on the website.
For example, change the back-to-source IP address of CDN or AAD to the WAF IP address by following the instructions shown in Figure 6.
Configure Subdomain Name and TXT Record.
Add a subdomain name and TXT record to the DNS records of your DNS provider by following the instructions shown in Figure 6.
Important
The high availability of our system, which is based on multi-AZ deployments to support both active-active and disaster recovery, relies on the WAF CNAME record.
If no proxy is used, the CNAME record must be configured. Figure 7 shows an example.
Figure 7 Connecting a domain name (CNAME record)¶
Go to your DNS provider and configure the CNAME record. For details, contact your DNS provider.
Important
The high availability of our system, which is based on multi-AZ deployments to support both active-active and disaster recovery, relies on the WAF CNAME record. Therefore,
Do not modify the hosts file. Add the CNAME record directly to the DNS records of your DNS provider.
Do not use the A record to replace the CNAME record.
The CNAME binding method of some common DNS providers is listed for your reference. If the following configuration is inconsistent with the actual configuration, rely on information provided by the DNS providers.
Log in to the management console of the DNS provider.
Go to the domain resolution record page.
Set the CNAME resolution record.
Set the record type to CNAME.
Generally, enter the domain name prefix in the host record. For example, if the protected domain name is admin.demo.com, enter admin in the host record.
The record value is the CNAME generated by WAF.
Resolution line: keep the default value TTL.
Click Save.
Important
The preceding resolution methods are provided by third parties. This document does not control or assume responsibility for any third party content, including but not limited to its accuracy, compatibility, reliability, availability, legitimacy, appropriateness, performance, non-infringement, or status update, unless otherwise specified in this document.
Verify that the CNAME has been configured.
In Windows, choose Start > Run. Then enter cmd and press Enter.
Run the following command to query the CNAME. If the configured CNAME is displayed, the configuration is successful.
nslookup www.domain.com
After the domain name is connected to WAF, click Next.
Click Finish.
You can view the DNS status and mode of the domain name in the domain list.
Note
If your web server is using other firewalls, disable the firewalls or whitelist the WAF IP address ranges.
If your web server is using personal security software, replace it with enterprise security software and whitelist the WAF IP address ranges.
If a domain name has been connected to WAF, DNS should be Normal. If DNS is Unconfigured, choose More > Check DNS in the Operation column of the target domain name to check the DNS status. If the problem persists, perform domain connection again by referring to What Should I Do If the DNS Status Is Unconfigured?
After a domain name is created, WAF protection is enabled by default. The mode of Basic Web Protection is Log only (detected attacks are only logged but not blocked.). WAF creates a CC attack protection rule for the domain name by default. The rule can be modified but cannot be deleted. Rate Limit in the rule is 500 requests/5 seconds by default and it can be adjusted up to 10000 requests/5 seconds. If you want a higher rate limit than the maximum value, contact the administrator.
Rules for Configuring Client Protocol and Server Protocol¶
WAF provides various protocol types. If your website is www.example.com, WAF provides the following four access modes:
HTTP mode. Figure 8 shows an example.
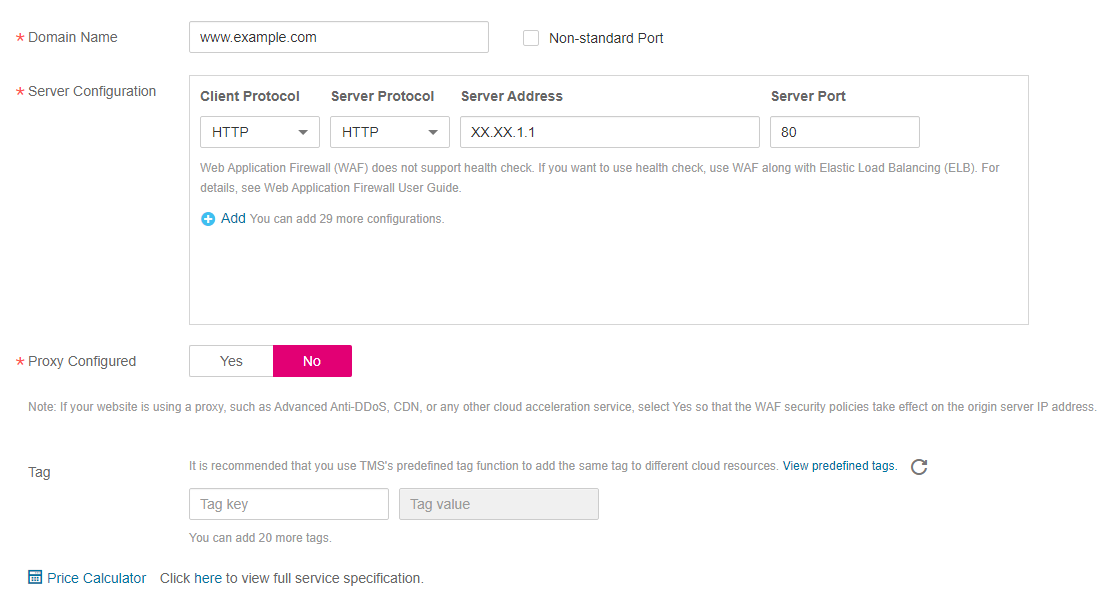
Figure 8 HTTP mode¶
Important
This configuration allows web visitors to access your website over HTTP only. If they access over HTTPS, they receive the 302 Found code and are redirected to http://www.example.com.
HTTPS mode. This configuration allows web visitors to access your website over HTTPS only. If they access over HTTP, they are redirected to https://www.example.com. Figure 9 shows an example.
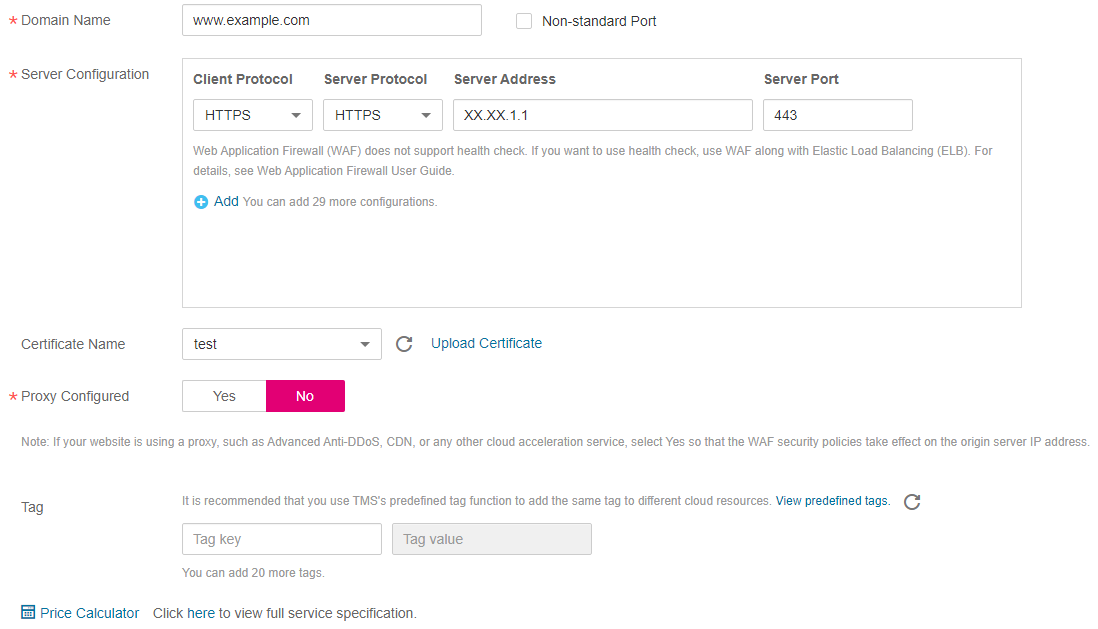
Figure 9 HTTPS mode¶
Important
If web visitors access your website over HTTPS, the website returns a successful response.
If web visitors access your website over HTTP, they receive the 302 Found code and are directed to https://www.example.com.
HTTP and HTTPS mode. Figure 10 shows an example.
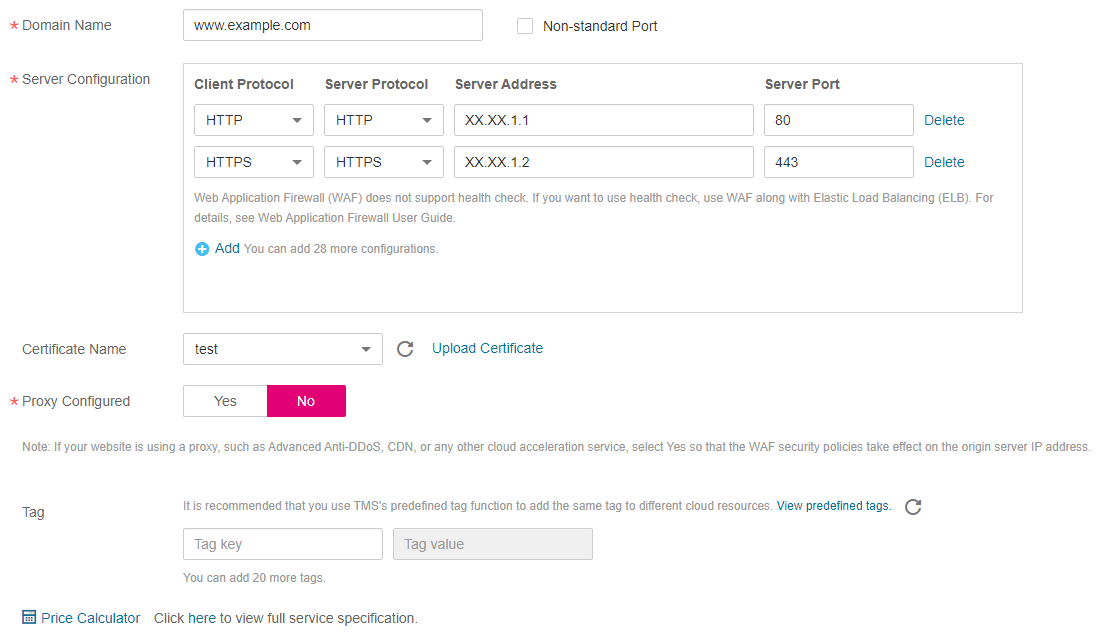
Figure 10 HTTP and HTTPS mode¶
Important
If web visitors access your website over HTTP, the website returns a successful response but no communication between the browser and website is encrypted.
If web visitors access your website over HTTPS, the website returns a successful response and all communications between the browser and website are encrypted.
HTTPS/HTTP mode. Figure 11 shows an example.
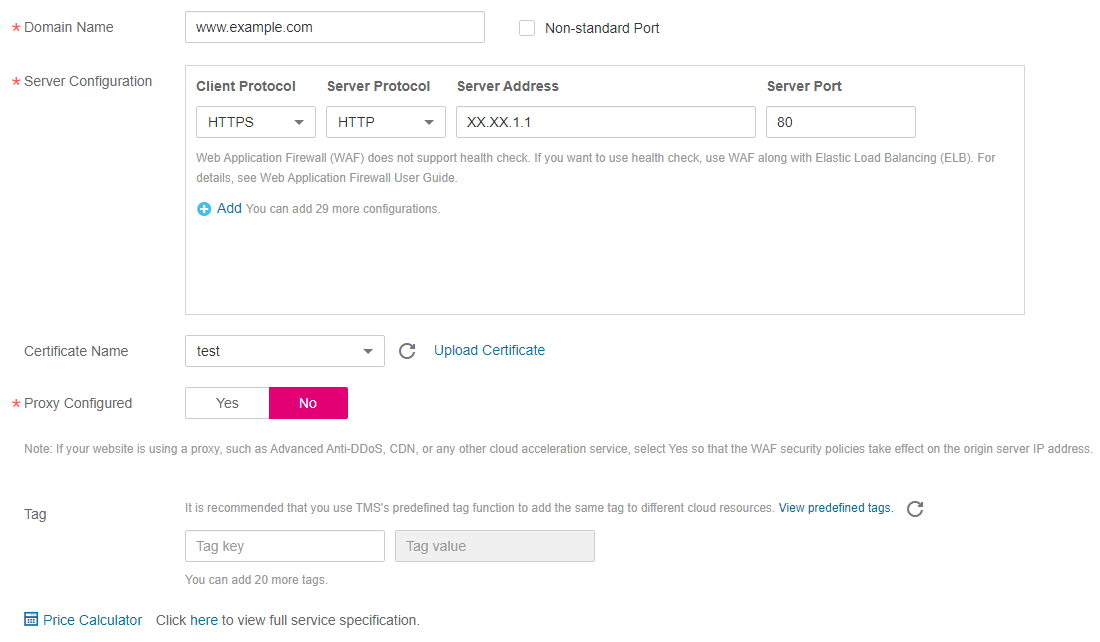
Figure 11 HTTPS/HTTP mode¶
Important
If web visitors access your website over HTTPS, WAF forwards the requests to your origin server over HTTP.