How to auto-generate security group¶
When two Bash components are in a connection relationship, the orchestration engine can auto-generate a security group to enable the traffic between them. For the auto generation of security groups, users specify the port property.
On the component
Bash_1, specify the port8080.On the component
Bash_2, specify the port27017.
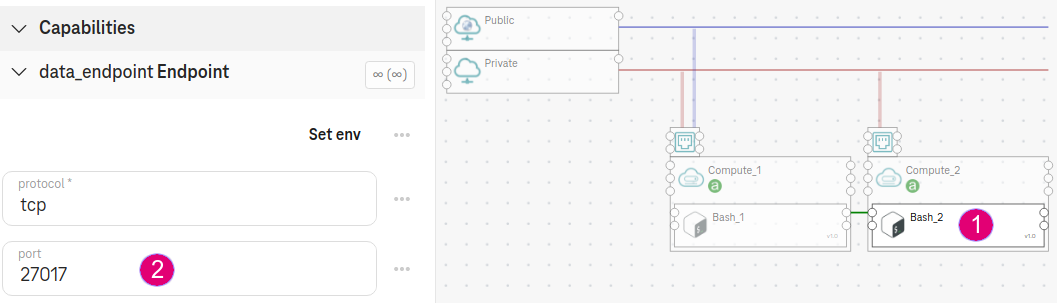
Figure 1. Specify the port property for auto-generated security group¶
Expected result:
Because
Compute_1is a public compute, a security group is generated for theCompute_1, which allows the traffic from the public network (i.e., allow theTCPprotocol from the remote IP0.0.0.0/0on port8080).Because
Bash_1connects toBash_2internally, a security group is generated for theCompute_2, which allows the private traffic from theCompute_1(i.e., allow theTCPprotocol from the remote security group ofCompute_1on port27017).The Open Telekom Cloud console also shows the auto-generated security groups attached to the ports of the two compute nodes. The figure below shows an example that the security group is auto-generated for the
Compute_2accordingly.
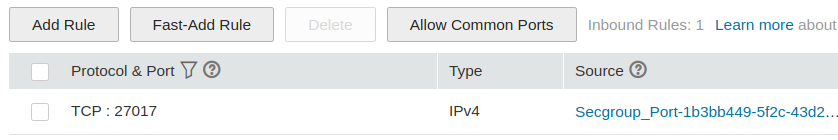
Figure 2. Example of auto-generated security group on the OTC console¶