Adjusting Security Settings¶
Scenarios¶
You can adjust security settings after Anti-DDoS is enabled.
Prerequisites¶
You have obtained an account and its password to log in to the management console.
Procedure¶
Log in to the management console.
Click
 in the upper left corner and select the desired region or project.
in the upper left corner and select the desired region or project.Under Security, choose Anti-DDoS. The Security Console is displayed.
Select the Public IP Addresses tab, locate the row that contains the IP address for which protection settings need to be modified, and click Set Protection in the Operation column, as shown in Figure 1.
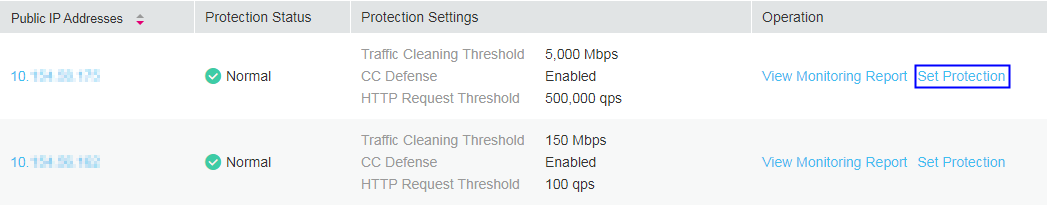
Figure 1 Public IP address list¶
In the displayed Set Protection dialog box, set required parameters, as shown in Figure 2.
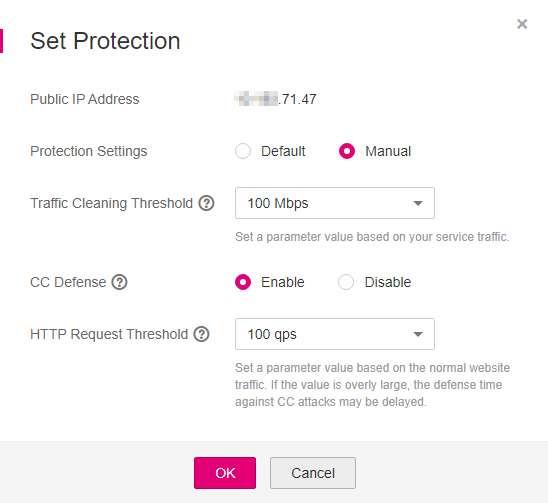
Figure 2 Page for setting protection parameters¶
Table 1 Parameter description¶ Parameter
Description
Protection Settings
Default: In this mode, Traffic Cleaning Threshold is fixed at 300 Mbps. When the service UDP traffic is greater than 300 Mbps or the TCP traffic is greater than 90000 pps, traffic scrubbing is triggered and Anti-DDoS will automatically intercept the attack traffic.
Manual: In this mode, you can set the value of Traffic Cleaning Threshold based on your service needs and enable CC Defense.
Note
Mbps = Mbit/s (short for 1,000,000 bit/s). It is a unit of transmission rate and refers to the number of bits transmitted per second.
PPS, short for Packets Per Second, is a measure of throughput for network devices. It means the number of packets sent per second.
Traffic Cleaning Threshold
Anti-DDoS scrubs traffic when detecting that the incoming traffic of an IP address exceeds the threshold.
The default value of Traffic Cleaning Threshold is fixed at 300 Mbps when Protection Settings is set to Default.
If you need to change the value of Traffic Cleaning Threshold, set Protection Settings to Manual. Then you can set the traffic cleaning threshold based on your service traffic. You are advised to set the threshold to a value closest to the purchased bandwidth but not greater than the purchased bandwidth.
If Traffic Cleaning Threshold is set to Unlimited, your public IP addresses get almost no protection from DDoS attacks.
Note
If your service traffic is larger than the value of Traffic Cleaning Threshold you set, traffic scrubbing is triggered. Only attack traffic is intercepted. If service traffic does not trigger scrubbing, no traffic is intercepted.
CC Defense
CC Defense is set to Disable automatically when Protection Settings is set to Default. Note that only CC Defense rather than Anti-DDoS protection is disabled.
If Protection Settings is set to Manual, you can enable CC Defense based on your service needs.
Note
CC defense is available only for clients that carry web services and support the full HTTP protocol stack. This is because CC defense works in redirection or redirection+verification code mode. If your client does not support the full HTTP protocol stack, you are advised to disable CC defense.
HTTP Request Threshold
This parameter is required only when CC Defense is set to Enable. The unit is qps (short for queries per second). QPS is a common measure of the amount of search traffic an information retrieval system, such as a search engine or a database, receives during one second.
This parameter is used to defend against a large number of malicious requests targeting websites. Defense against CC attacks, which aim to exhaust server resources by sending specially crafted GET or POST requests, is triggered when the HTTP request rate on a site reaches the selected value. In EIP protection, the maximum recommended value is 5000. In ELB protection, the value can be larger
You are advised to set this parameter to the maximum number of HTTP requests that can be processed by the deployed service. Anti-DDoS will automatically scrub traffic if detecting that the total number of requests exceeds the configured HTTP request threshold. If the value is too large, CC defense will not be triggered promptly.
If the actual HTTP request rate is smaller than the configured value, the deployed service is able to process all HTTP requests, and Anti-DDoS does not need to be involved.
If the actual HTTP request rate is greater than or equal to the configured value, Anti-DDoS triggers CC defense to analyze and check each request, which affects responses to normal requests.
Click OK to save the settings.