Configuring the Network¶
Public Access¶
By default, functions can access services on public networks. If the target public network service requires whitelist verification using a fixed IP address, enable VPC access, configure a NAT gateway for the VPC, and bind an Elastic IP (EIP) to the gateway. For details, see Configuring a Fixed Public IP Address
Configuring VPC Access¶
Functions can access resources in a VPC bound to it. If a function needs both VPC and public access, configure a NAT gateway for the VPC and bind an EIP to the gateway. For details, see Configuring a Fixed Public IP Address.
Required Permissions
Configure an agency by referring to Configuring Agency Permissions.
Permissions for VPC access: an agency with the VPC Administrator permission or with the least permissions listed in Table 1
Table 1 Least permissions required¶ Permission
Action
Deleting a port
vpc:ports:delete
Querying a port
vpc:ports:get
Creating a port
vpc:ports:create
Querying a VPC
vpc:vpcs:get
Querying a subnet
vpc:subnets:get
Permissions for private domain name resolution: an agency with the DNS ReadOnlyAccess permission
Procedure
Log in to the FunctionGraph console. In the navigation pane, choose Functions > Function List.
Click the function to be configured to go to the function details page.
Choose Configuration > Network, enable VPC Access, and specify a VPC and subnet.
To enable VPC Access, you need to configure the following inbound and outbound rules in the default security group. For details, see section "Adding a Security Group Rule".
Inbound rule: Set Action to Allow, Protocol & Port to ICMP, and the minimum range for Source to the VPC CIDR block selected for the function. For example, if the VPC CIDR block of the function is 192.168.x.x/24, add an inbound rule with Allow for Action, ICMP for Protocol & Port, and 192.168.x.x/24 for Source.
Outbound rule: Set Action to Allow.
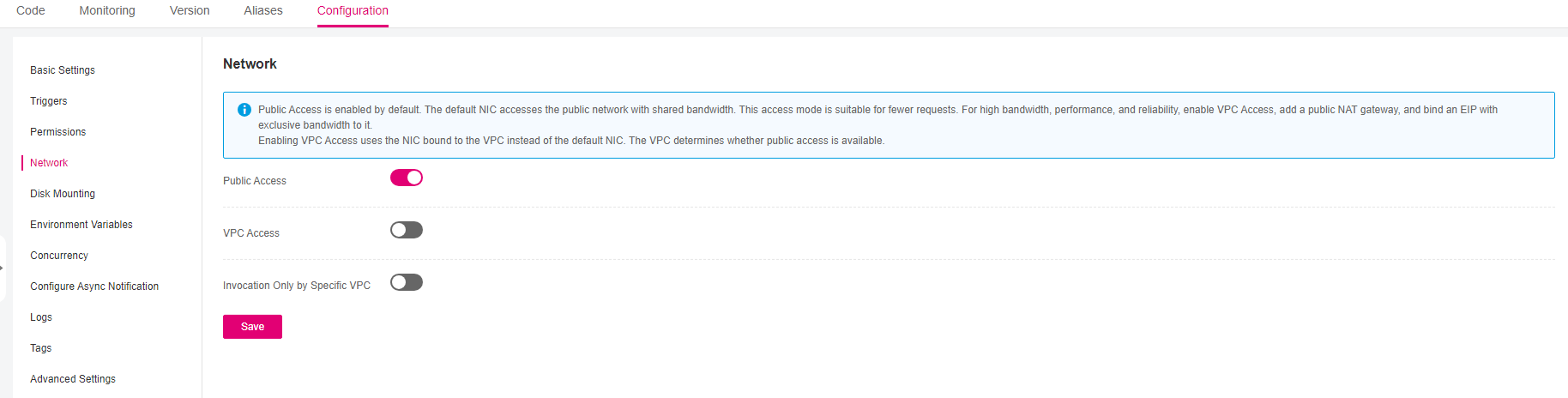
Figure 1 Configuring VPC access¶
Note
For details on how to create a VPC and a subnet, see Creating a VPC.
Specify an agency with VPC administrator permissions for the function. For details, see Configuring Agency Permissions.
All functions of a tenant in a project can be bound to a maximum of four subnets. (Each project has a unique 32-digit project ID, which is allocated when your account is created. The project IDs of your account and IAM user are the same.)
(Optional) Configure the domain name.
Enter one or more private domain names of the VPC so that the function can use them to access resources in this VPC. See Figure 1.
Note
For details about how to create a private domain name, see Creating a Private Zone.
Functions can resolve only domain names of the A record set type. For details about how to add a record set, see Record Set Types and Configuration Rules.
(Optional) Configure the VPC CIDR block.

Figure 2 VPC CIDR block¶
Note
You can enter the VPC CIDR block used in the code to check whether it conflicts with FunctionGraph's VPC CIDR block.
Click Save.
Configuring a Fixed Public IP Address¶
If a function needs to access public network resources in a VPC or requires a fixed public IP address, configure a NAT gateway for the VPC and bind an EIP to the gateway.
Prerequisites
You have created a VPC and a subnet according to Creating a VPC.
You have obtained an EIP according to Assigning an EIP.
Procedure
In the left navigation pane of the management console, choose Network > NAT Gateway to go to the NAT Gateway console. Then click Create NAT Gateway.
On the displayed page, enter gateway information, select a VPC (for example, vpc-01) and subnet, and confirm and submit the settings. For details, see Creating a Public NAT Gateway.
Click the NAT gateway name. On the details page that is displayed, click Add SNAT Rule, set the rule, and click OK.