Configuring Agency Permissions¶
Overview¶
FunctionGraph works with other cloud services in most scenarios. Create a cloud service agency so that FunctionGraph can perform resource O&M in other cloud services on your behalf.
Scenario¶
Before using FunctionGraph in the following scenarios, create an agency. Adjust the permissions granted to the agency to meet your service requirements. For example, grant the Admin permission in the development phase, and change it to the fine-grained minimum permission in the product environment. This ensures the required permissions while eliminating risks. Select the required action by referring to Table 1.
Scenario | Admin Permission | Fine-Grained Minimum Permission | Description |
|---|---|---|---|
Using a custom image | SWR Administrator | Unavailable | SWR Admin: administrator who has all permissions for the Software Repository for Container (SWR) service. For details about how to create a custom image, see Creating a Function with an Image. |
Mounting an SFS Turbo file system | SFS Turbo ReadOnlyAccess | sfsturbo:shares:getShare (Query details about a file system) sfsturbo:shares:showFsDir (Check whether a directory exists) | SFS Turbo ReadOnlyAccess: read-only permissions for SFS Turbo. sfsturbo:shares:getShare: permission for querying a file system in SFS. sfsturbo:shares:showFsDir: permission for checking whether a directory exists in SFS. For details about how to mount an SFS Turbo file system, see Mounting an SFS Turbo File System. |
Mounting an ECS shared directory | ECS ReadOnlyAccess | ecs:cloudServers:get (Query details about an ECS) | ECS ReadOnlyAccess: read-only permissions for ECS. ecs:cloudServers:get: permission for querying an ECS. For details about how to mount an ECS shared directory, see Mounting an ECS Shared Directory. |
Configuring a reserved instance policy | AOM ReadOnlyAccess | aom:metric:get (Query a metric) aom:metric:list (Query metric list) | AOM ReadOnlyAccess: read-only permissions for AOM. aom:metric:get: permissions for querying a metric in AOM. aom:metric:list: permissions for querying metric list in AOM. |
Using a DMS trigger | DMS ReadOnlyAccess | dms:instance:get (Query instance details) | DMS ReadOnlyAccess: read-only permissions for DMS. dms:instance:get: permissions for querying instance details in DMS. |
Configuring cross-domain VPC access | VPC Administrator | vpc:ports:get (Query a port) vpc:ports:create (Create a port) vpc:vpcs:get (Query a VPC) vpc:subnets:get (Query a subnet) vpc:vips:delete (Unbind a virtual IP address from a VM) vpc:securityGroups:get (Query security groups or details about a security group) | Users with the VPC Administrator permissions can perform any operations on all cloud resources of the VPC. To configure cross-VPC access, specify an agency with VPC management permissions. Fine-grained minimum permission for VPC: permissions for unbinding a virtual IP address from a VM, querying a port, creating a port, querying a VPC, querying a subnet, and querying security groups or details about a security group. For details about how to configure cross-domain VPC access, see Configuring Networks. |
Configuring asynchronous notification | If the target service is OBS: OBS Administrator | obs:bucket:HeadBucket (Obtain bucket metadata) obs:bucket:CreateBucket (Create a bucket) obs:object:PutObject (Upload objects using PUT method, upload objects using POST method, copy objects, append an object, initialize a multipart task, upload parts, and merge parts) | OBS Administrator: administrator who has all permissions for OBS. Fine-grained minimum permission for OBS: permissions for obtaining bucket metadata, creating a bucket, uploading objects using POST method, copying objects, appending an object, initializing a multipart task, uploading parts, and merging parts. For details about how to configure asynchronous notification, see Configuring Asynchronous Notification Policy. |
If the target service is SMN: SMN Administrator | smn:topic:publish (Publish a message) smn:topic:list (Query the topic list) | SMN Administrator: administrator who has all permissions for SMN. Fine-grained minimum permission for using SMN: permissions for publishing a message and querying the topic list. For details about how to configure asynchronous notification, see Configuring Asynchronous Notification Policy. |
Creating an Agency¶
Note
In the following example, the VPC Administrator permission is assigned to FunctionGraph and this setting takes effect only in the authorized regions.
Create an agency by referring to section "Creating an Agency" and set parameters as follows:
Log in to the IAM console.
On the IAM console, choose Agencies from the navigation pane, and click Create Agency in the upper right corner.
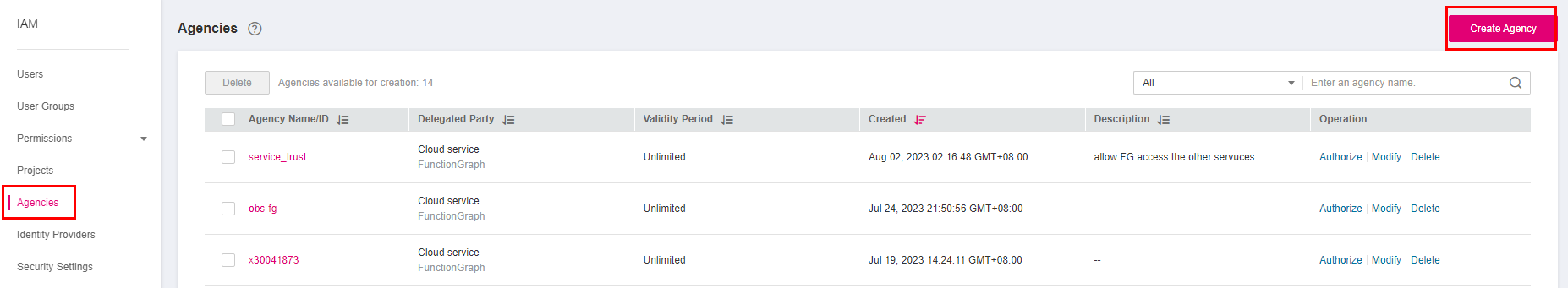
Figure 1 Creating an agency¶
Configure the agency.
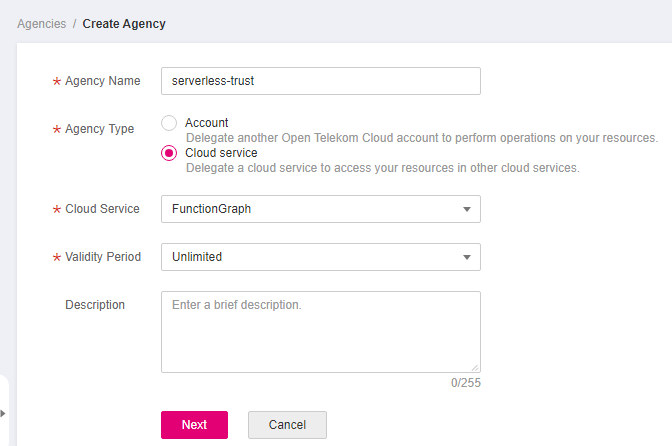
Figure 2 Setting basic information¶
For Agency Name, enter serverless-trust.
For Agency Type, select Cloud service.
For Cloud Service, select FunctionGraph.
For Validity Period, select Unlimited.
Description: Enter the description.
Click Next. On the displayed page, search for the permissions to be added in the search box on the right and select the permissions. The VPC Administrator permission is used as an example.
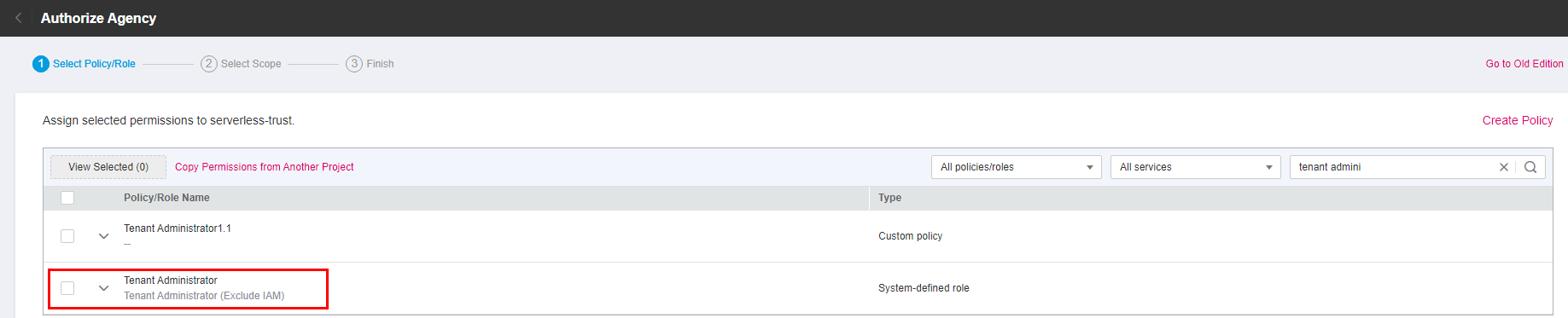
Figure 3 Selecting policies¶
Table 2 Example of agency permissions¶ Policy Name
Scenario
VPC Administrator
VPC administrator
Click Next and select the scope.
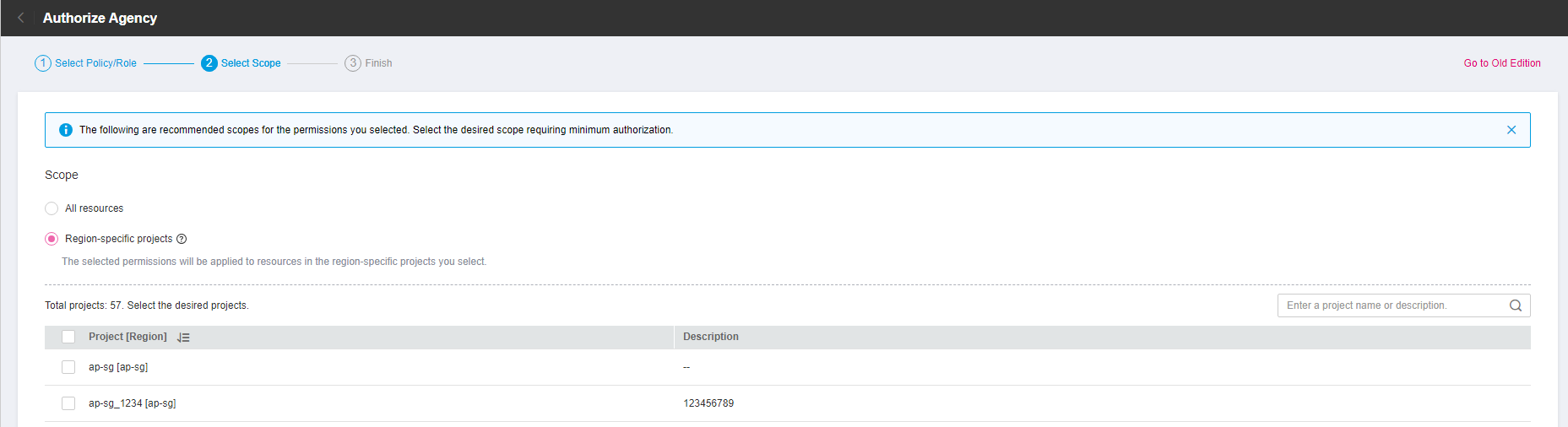
Figure 4 Selecting the required permissions¶
Configuring an Agency¶
In the left navigation pane of the management console, choose Compute > FunctionGraph. On the FunctionGraph console, choose Functions > Function List from the navigation pane.
Click the function to be configured to go to the function details page.
Choose Configuration > Permissions, click Create Agency, and set an agency based on site requirements by referring to 2
-5.Table 3 Agency configuration parameters¶ Parameter
Description
Agency
Select a function that you have created.
Execution Agency
Mandatory if you select Specify an exclusive agency for function execution.
Note
To ensure optimal performance, select Specify an exclusive agency for function execution and set different agencies for function configuration and execution. You can also use no agency or specify the same agency for both purposes. Figure 5 shows the agency options.
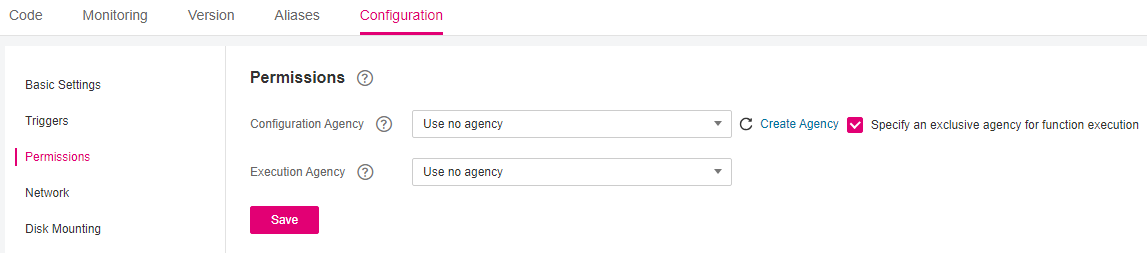
Figure 5 Setting agencies¶
Execution Agency: This type of agency enables you to obtain a token and AK/SK from the context in the function handler for accessing other cloud services.
Click Save.
Modifying an Agency¶
Modifying an agency: You can modify the permissions, validity period, and description of an agency on the IAM console.
Caution
After an agency is modified, it takes about 10 minutes for the modification (for example, context.getToken) to take effect.
The agency information obtained using the context method is valid for 24 hours. Refresh it before it expires.