How to define a bastion host¶
Connect all computes to the admin network (step 1).
Drop the SSHBastionHost component on one compute (step 2). The given compute is now the bastion host.
Also connect the bastion host to the public network.
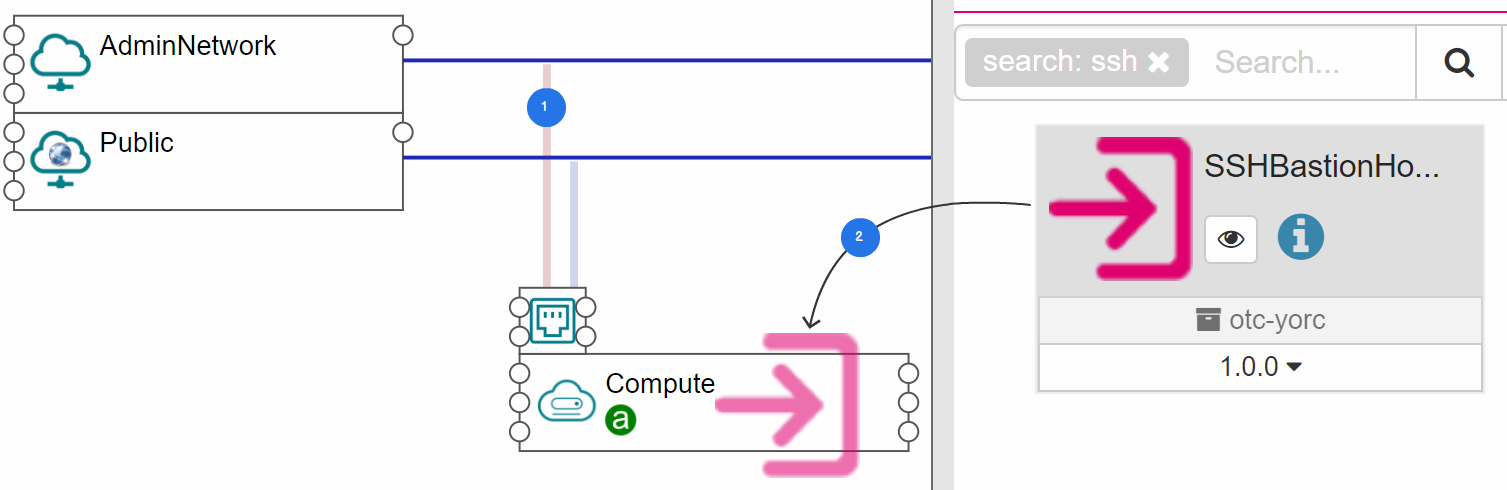
Figure 1. Define a compute node as a bastion host¶
Note
If you forgot to connect the bastion host to the admin network, the designer will automatically connect it to the admin network for you.
Expected result¶
During the deployment, the orchestration engine creates the security group
Secgroup_BastionHoston the bastion host, which allowsTCPincoming traffic on port22from the remote IP of the orchestration engine. As a result, it can connect to the bastion host over the public network (step 1).The orchestration engine uses the bastion host as a jump host to SSH to the private
Compute_2in the admin network and deploy the service catalogHelloWorld(step 2). To accessCompute_2over the bastion host, the orchestrator creates the security groupSecgroup_AdminonCompute_2, which allows incoming traffic from the remoteSecgroup_BastionHoston port22. It also enablesTCP forwardingon the bastion host.After the deployment completes, the orchestration engine deletes the security group rule on the bastion host to prevent any further access to the bastion host.
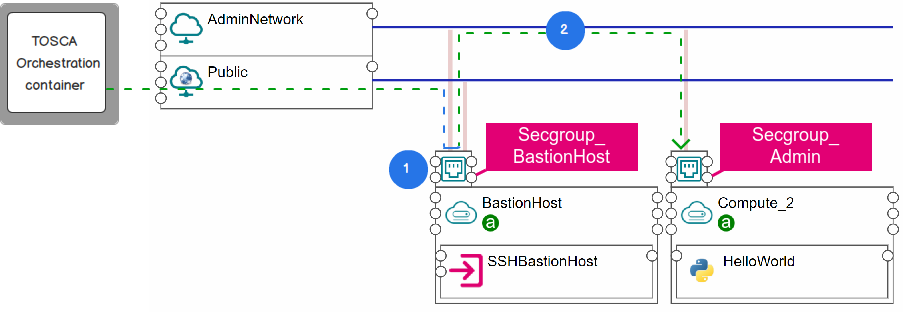
Figure 2. The deployment flows¶
Note
Auto-select Bastion Host: If users do not define a bastion host explicitly, the designer will auto-select a compute node connecting to the public network as the bastion host. It also warns the users, which compute node is chosen as the bastion host before the deployment:
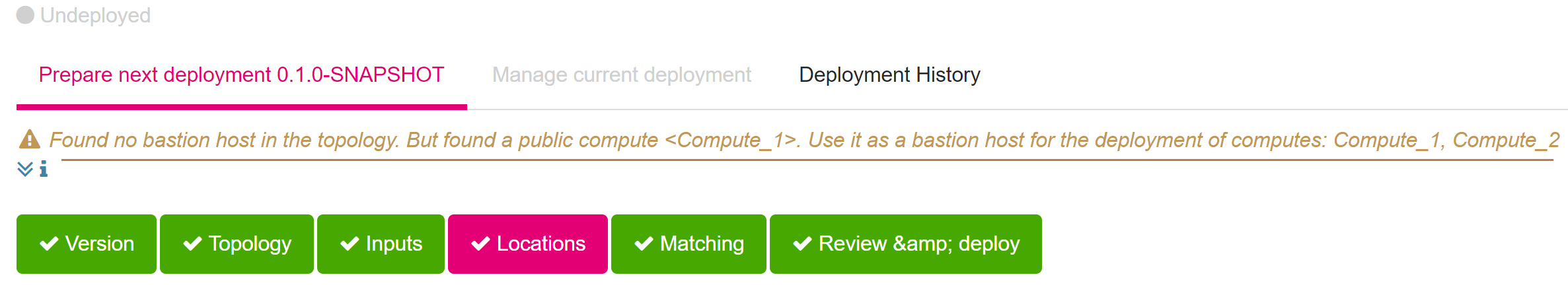
Figure 2. A warning message that a bastion host is auto selected before the deployment¶