Creating a User and Granting Permissions¶
This section describes how to use IAM to implement fine-grained permissions control for RF service. With IAM, you can:
Create IAM users for employees based on your organizational structure. Each IAM user has their own security credentials for accessing RF service.
Granting users only the permissions required to perform a given task based on their job responsibilities.
Entrust an account or a cloud service to perform operations for your RF service.
If your account does not need indivitual IAM users, skip this section.
Figure 1 shows the process flow for granting permissions.
Prerequisites
Before granting permissions, learn about the RFS permissions and select the permissions as required. For details about the system-defined permissions supported by RFS, see RFS Permissions. To grant permissions for other services, you can see permissions.
Flowchart
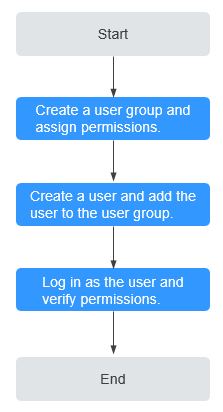
Figure 1 Granting RFS permissions¶
On the IAM console, create a user group and assigning permissions. Here, RFS ReadOnlyAccess permissions are used as an example.
Log in and verify permissions.
The created user logs in to the console and verifies permissions as described below:
Choose Service List > Resource Formation Service. In the navigation pane on the left, click on Stacks. If you can view the stack list successfully, the RFS ReadOnlyAccess policy is in effect. If you click on Create Stack in the upper right corner of the displayed page, you should receive a notification message indicating your insufficient permissions.
Choose another service from Service List. If a message appears indicating that you have insufficient permissions to access the service, it also reflects the RFS ReadOnlyAccess policy.