IAM Policies¶
You can create IAM users under a registered cloud service account, and then use IAM policies to control users' access permissions to cloud resources.
IAM policies define the actions that can be performed on your cloud resources. In other words, IAM policies specify what actions are allowed or denied.
IAM policies with OBS permissions take effect on all OBS buckets and objects. To grant an IAM user the permission to operate OBS resources, you need to assign one or more OBS permission sets to the user group to which the user belongs.
For details about OBS permissions controlled by IAM policies, see Permissions Management.
IAM policies Application Scenarios¶
IAM policies are used to authorize IAM users under an account.
Controlling permissions to cloud resources as a whole under an account
Controlling permissions to all OBS buckets and objects under an account
Policy Structure and Syntax¶
A policy consists of a version and statements. Each policy can have multiple statements.
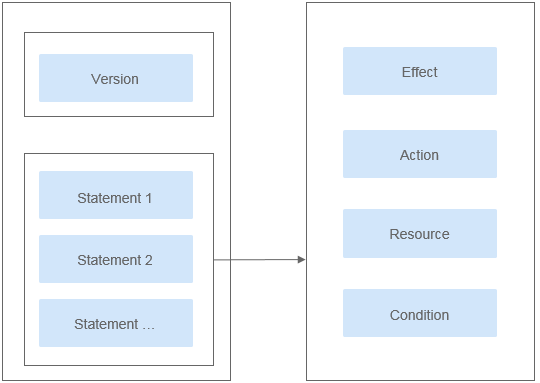
Figure 1 Policy structure¶
Policy syntax example:
{
"Version": "1.1",
"Statement": [
{
"Effect": "Allow",
"Action": [
"obs:bucket:HeadBucket",
"obs:bucket:ListBucket",
"obs:bucket:GetBucketLocation"
],
"Resource": [
"obs:*:*:bucket:*"
],
"Condition": {
"StringEndWithIfExsits": {
"g:UserName": ["specialCharacter"]
},
"Bool": {
"g:MFAPresent": ["true"]
}
}
}
]
}
Parameter | Description |
|---|---|
Version | The version number of a policy.
|
Statement | Permissions defined by a policy, including Effect, Action, Resource, and Condition. Condition is optional.
|
Authentication of IAM policies¶
The authentication of IAM policies starts from the Deny statements. The following figure shows the authentication logic for resource access.
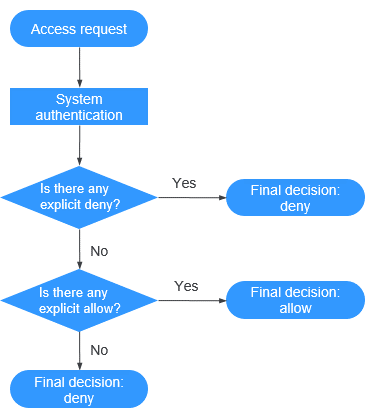
Figure 2 Authentication logic¶
Note
The actions in each policy are in the OR relationship.
A user accesses the system and makes an operation request.
The system evaluates all the permission policies assigned to the user.
In these policies, the system looks for explicit deny permissions. If the system finds an explicit deny that applies, it returns a decision of Deny, and the authentication ends.
If no explicit deny is found, the system looks for allow permissions that would apply to the request. If the system finds an explicit allow permission that applies, it returns a decision of Allow, and the authentication ends.
If no explicit allow permission is found, IAM returns a decision of Deny, and the authentication ends.