Managing the Vulnerability Whitelist¶
If you evaluate that some vulnerabilities do not affect your services and do not want to view the vulnerabilities in the vulnerability list, you can whitelist the vulnerabilities. After they are whitelisted, the vulnerabilities will be ignored in the vulnerability list and no alarms will be reported. The vulnerabilities will not be scanned and the vulnerability information will not be displayed when the next vulnerability scan task is executed.
This section describes how to whitelist a vulnerability, modify a vulnerability whitelist rule, and remove a vulnerability whitelist rule from the vulnerability whitelist.
Whitelisting Vulnerabilities¶
Log in to the management console.
In the navigation pane, choose Prediction > Vulnerabilities.
Whitelisting all servers that are affected by a vulnerability
HSS will ignore the vulnerability when scanning for vulnerabilities on all servers.
In the Operation column of the row containing the target vulnerability, click More and select Add to Whitelist.
You can also select multiple vulnerabilities and click Add to Whitelist above the vulnerability list.
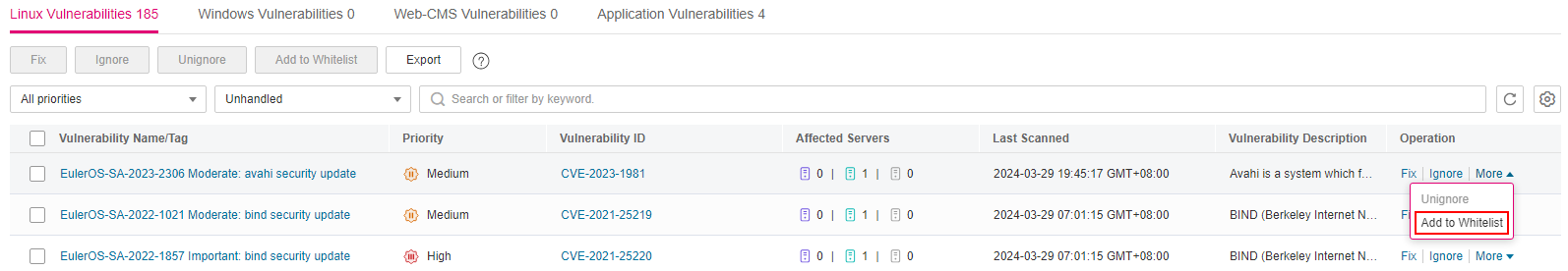
Figure 1 Whitelisting all servers that are affected by a vulnerability¶
In the dialog box displayed, click OK.
Whitelisting one or more servers that are affected by a vulnerability
HSS will ignore the vulnerability when scanning for vulnerabilities on these servers.
Click a target vulnerability name.
On the slide-out panel displayed, click the Affected tab.
In the Operation column of the row containing the target server, click More and select Add to Whitelist.
You can also select multiple servers and click Add to Whitelist above the server list.
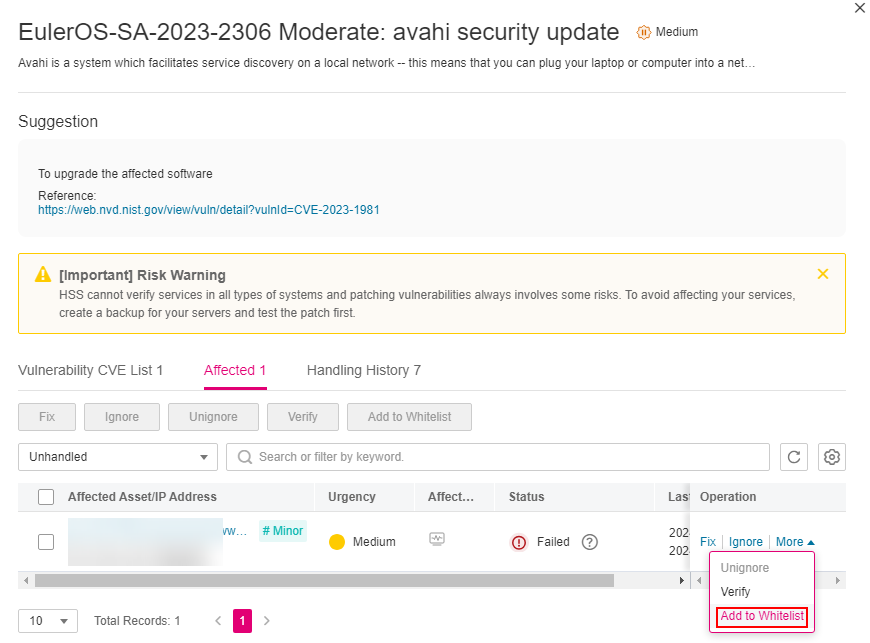
Figure 2 Whitelisting a single server that is affected by a vulnerability¶
In the dialog box displayed, click OK.
Whitelisting vulnerabilities using whitelist rules
In the upper right corner of the Vulnerabilities page, click Configure Policy. The Configure Policy slide-out panel is displayed.
In the Vulnerability Whitelist area, click Add Rule.
Configure a whitelist rule according to Table 1.
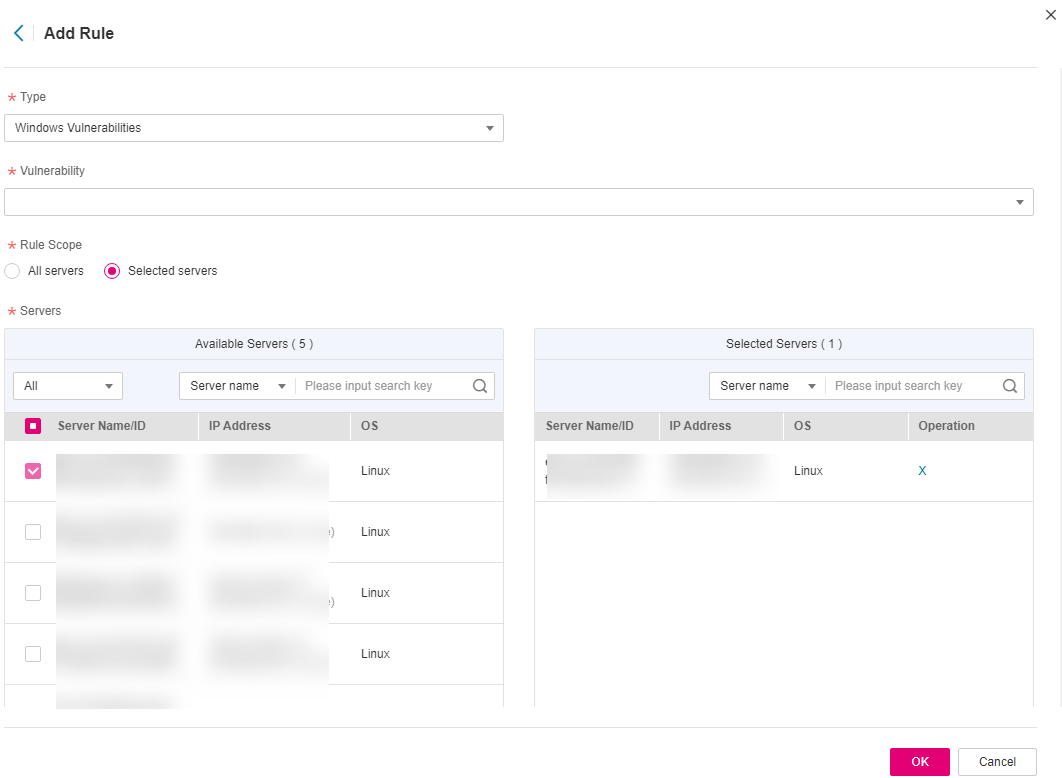
Figure 3 Configuring a whitelist rule¶
Table 1 Vulnerability whitelist rule parameters¶ Parameter
Description
Type
Select the type of vulnerabilities to be whitelisted. Possible values are as follows:
Linux Vulnerabilities
Windows Vulnerabilities
Web-CMS Vulnerabilities
Application Vulnerabilities
Vulnerability
Select one or more vulnerabilities to be whitelisted.
Rule Scope
Select the servers affected by the vulnerabilities. Possible values are as follows:
All servers
HSS will ignore the vulnerability when scanning for vulnerabilities on all servers.
Selected servers
Select one or more target servers. HSS will ignore the vulnerabilities when scanning for vulnerabilities on these servers.
You can search for a target server by server name, ID, EIP, or private IP address.
Remarks (Optional)
Enter the remarks.
Click OK.
Editing a Vulnerability Whitelist¶
Log in to the management console.
In the navigation pane, choose Prediction > Vulnerabilities.
In the upper right corner of the Vulnerabilities page, click Configure Policy. The Configure Policy slide-out panel is displayed.
In the row containing the desired vulnerability whitelist rule, click Edit in the Operation column.
On the editing page, modify the information and click OK.
Removing a Vulnerability Whitelist Rule from the Vulnerability Whitelist¶
Log in to the management console.
In the navigation pane, choose Prediction > Vulnerabilities.
In the upper right corner of the Vulnerabilities page, click Configure Policy. The Configure Policy slide-out panel is displayed.
In the row containing the desired vulnerability whitelist rule, click Delete in the Operation column.
In the dialog box displayed, confirm the information and click OK.