Container Cluster Protection Overview¶
HSS can check for non-compliance baseline issues, vulnerabilities, and malicious files when a container image is started and report alarms on or block container startup that has not been unauthorized or may incur high risks.
You can configure container cluster protection policies to block images with vulnerabilities, malicious files, non-compliant baselines, or other threats, hardening cluster security.
Constraints and Limitations¶
Container cluster protection is available only in the HSS container edition.
To use container cluster protection, ensure the agent installed on the server falls within the following range. For details about how to upgrade the agent, see Upgrading the Agent.
Linux: 3.2.7 or later
Windows: 4.0.19 or later
Process of Using Container Cluster Protection¶
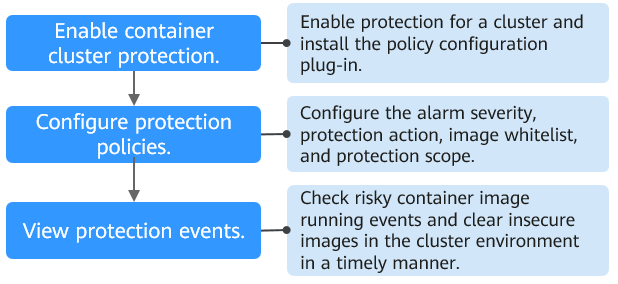
Figure 1 Usage process¶
Operation | Description |
|---|---|
Enable protection for a cluster to protect its workloads and critical data. When protection is enabled, HSS automatically installs the policy management plug-in on the cluster. | |
Configure the severity of baseline, vulnerability, and malicious file risks that trigger alarms; container cluster protection scope; image whitelist; and actions to be taken on alarms. | |
On the HSS console, you can view unauthorized or high-risk container image running events that are reported or blocked, and check and clear insecure container images in a timely manner. |