Creating a User and Granting Permissions¶
This section describes IAM's fine-grained permissions management for your HSS resources. With IAM, you can:
Create IAM users for employees based on the organizational structure of your enterprise. Each IAM user has their own security credentials, providing access to HSS resources.
Grant only the permissions required for users to perform a specific task.
Entrust a cloud account or cloud service to perform professional and efficient O&M on your HSS resources.
If your account does not require individual IAM users, skip this chapter.
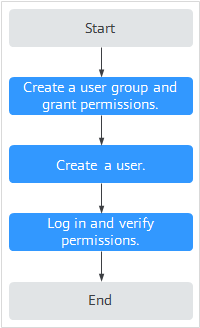
This section describes the procedure for granting permissions (see Figure 1).
Prerequisite¶
Before authorizing permissions to a user group, you need to know which HSS permissions can be added to the user group. Table 1 describes the policy details.
Role/Policy Name | Description | Type | Dependency |
|---|---|---|---|
HSS Administrator | HSS administrator, who has all permissions of HSS | System-defined role |
|
HSS FullAccess | All HSS permissions | System-defined policy | None |
HSS ReadOnlyAccess | Read-only permission for HSS | System-defined policy | None |