Managing SWR Private Images¶
Images in the private image repository come from SWR images. You can manually scan for and check reports on vulnerabilities, malicious files, software information, file information, baseline check, sensitive information.
Constraints¶
Only the HSS container edition supports this function.
Security scans can be performed only on Linux images.
Viewing Private Images¶
Log in to the management console.
Click
 in the upper left corner of the page, select a region, and choose Security > HSS. The HSS page is displayed.
in the upper left corner of the page, select a region, and choose Security > HSS. The HSS page is displayed.In the navigation pane, choose Asset Management Container & Quota. On the displayed page, click the Container Images tab and click SWR private image.
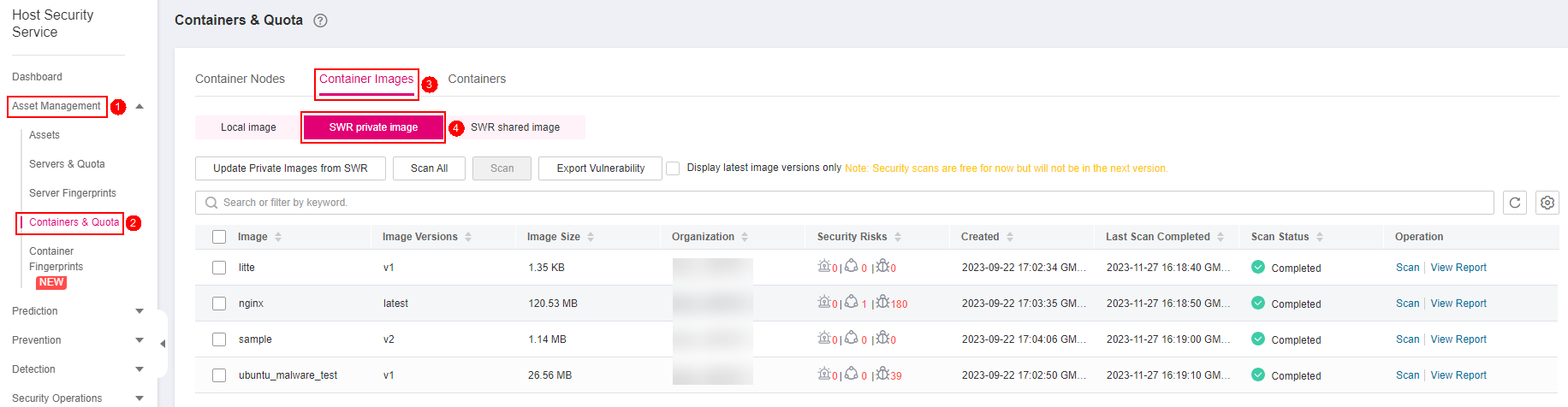
Figure 1 Accessing the private image list¶
You can click Update Private Images from SWR to update self-owned images from SWR.
Scanning a Private Image¶
You can choose all images, multiple images, or a single image and manually start a scan. The duration of a security scan depends on the scanned image size. Generally, scanning an image takes shorter than 3 minutes. After the scan is complete, click View Report to check the report.
Scan items of private images in SWR are as follows:
Scan Item | Description |
|---|---|
Vulnerability | Detect system and application vulnerabilities in images. |
Malicious file | Detects malicious files in images. |
Software information | Collects software information in an image. |
File information | Collects file information in an image. |
Unsafe setting |
|
Sensitive information | Detects files that contain sensitive information in images.
|
Software compliance | Detects software and tools that are not allowed to be used. |
Basic image information | Detects service images that are not created using base images. |
Log in to the management console and go to the HSS page.
In the navigation pane, choose Asset Management > Containers & Quota.
Click the Container Images tab and select Private images. In the Operation column of an image, click Scan.
In the displayed dialog box, click OK to start the scan job.
Scanned in the Scan Status column indicates the target image scan completed.