Kafka Authentication¶
PLAINTEXT¶
No security authentication mode is available. You only need to enter the IP address and port for connection.
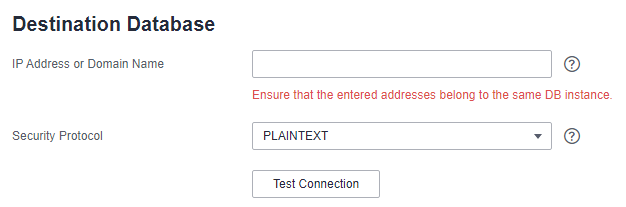
Figure 1 PLAINTEXT¶
SASL_PLAINTEXT¶
The SASL mechanism is used to connect to Kafka, and you need to configure SASL parameters.
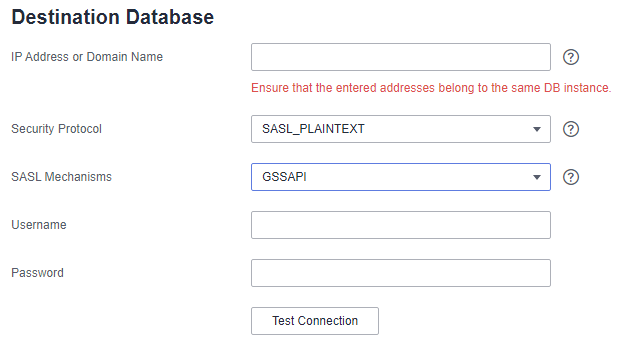
Figure 2 SASL_PLAINTEXT¶
Parameter | Description |
|---|---|
SASL Mechanisms | SASL is used by client. The following four items are supported. Kafka server uses the GSSAPI mechanism by default.
|
Token Delegation | Whether an agency token is used for authentication. This option is available when SCRAM-SHA-256 or SCRAM-SHA-512 is selected for SASL Mechanisms. |
Username | Username for logging in to the database |
Password | Password for the username |
SSL¶
SSL is used to encrypt the connection to Kafka. Related parameters need to be configured.
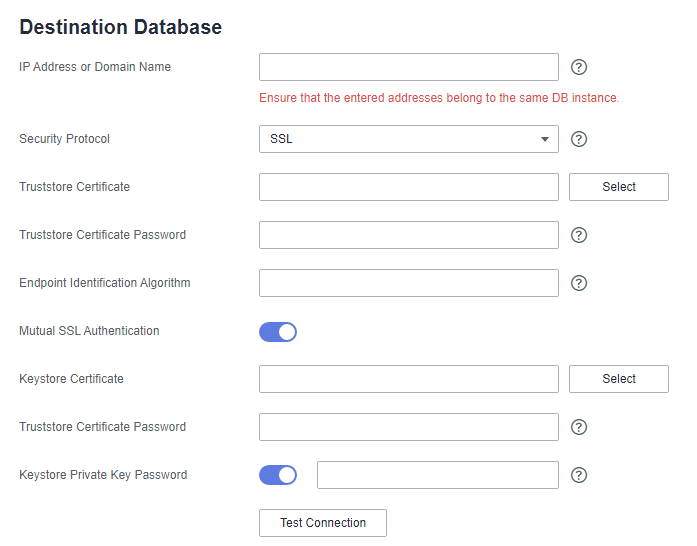
Figure 3 SSL¶
Parameter | Description |
|---|---|
Truststore Certificate | SSL certificate with the file name extension .jks. |
Truststore Certificate Password | Password of the certificate |
Endpoint Identification Algorithm | Endpoint identification algorithm for verifying the host name of the server using the server certificate. This parameter is optional. If this parameter is left blank, host name verification is disabled. |
Mutual SSL Authentication | Mutual SSL Authentication |
Keystore Certificate | If mutual SSL authentication is enabled, you need to upload the mutual SSL authentication certificate with the file name extension .jks. |
Keystore Certificate Password | Password of the mutual SSL authentication certificate. This option is available if mutual SSL authentication is enabled. |
Keystore Private Key Password | (Optional) Password of the private key in the keystore certificate. |
SASL_SSL¶
If the SASL and SSL are used, configure SSL and SASL parameters. For details, see SASL_PLAINTEXT and SSL.
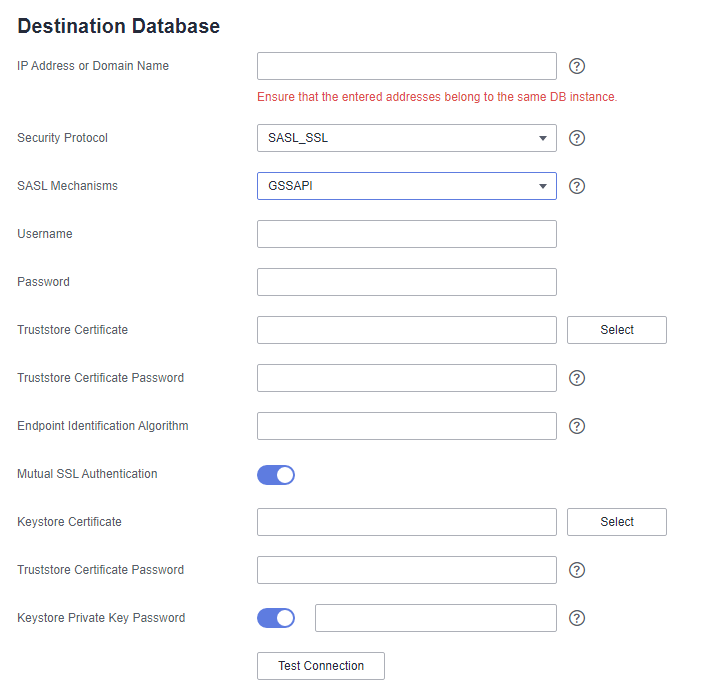
Figure 4 SASL_SSL¶