Permission Management¶
If you need to assign different permissions to employees in your enterprise to access your DataArts Studio resources, IAM is a good choice for fine-grained permissions management. IAM provides identity authentication, permissions management, and access control, helping you secure access to your resources.
With IAM, you can use your account to create IAM users for your employees, and assign permissions to the users to control their access to specific resource types. For example, if you want to allow some software developers in your enterprise to use DataArts Studio resources but disallow them to delete workspaces or perform any high-risk operations, you can create IAM users for the software developers and grant them only the permissions required for using DataArts Studio resources.
DataArts Studio Permissions¶
New IAM users do not have any permissions assigned by default. You need to first add them to one or more groups and then attach policies or roles to these groups. After authorization, the users can perform specified operations.
DataArts Studio is a project-level service deployed in specific physical regions. To assign permissions to a user group, specify the scope as region-specific projects and select projects for the permissions to take effect. If All projects is selected, the permissions will take effect for the user group in all region-specific projects. When accessing DataArts Studio, users need to switch to a region where they are authorized to use cloud services.
DataArts Studio supports only system role-based authorization and does not support policy-based authorization. To implement fine-grained permission control, DataArts Studio provides the capability of granting permissions to system roles and workspace roles. Specific operation permissions are granted to workspace roles, and workspace roles with different permissions can be customized.
Note
IAM provides the following two authorization mechanisms: Note that DataArts Studio supports only the IAM role-based authorization and does not support the IAM policy-based authorization.
IAM Roles: IAM initially provides a coarse-grained authorization mechanism to define permissions based on users' job responsibilities. Only a limited number of service-level roles are available. However, traditional IAM roles are not an ideal choice for fine-grained authorization and secure access control.
IAM Policies: A type of fine-grained authorization mechanism that defines permissions required to perform operations on specific cloud resources under certain conditions. This type of authorization is more flexible and is ideal for least privilege access.
As shown in Figure 1 and Table 1 and Table 1, the system-defined roles supported by DataArts Studio include DARTS Administrator and DARTS User. Workspace roles are based on the DARTS User. Permissions lists the common operations supported by DataArts Studio and the permissions granted to each role. You can select roles as required.
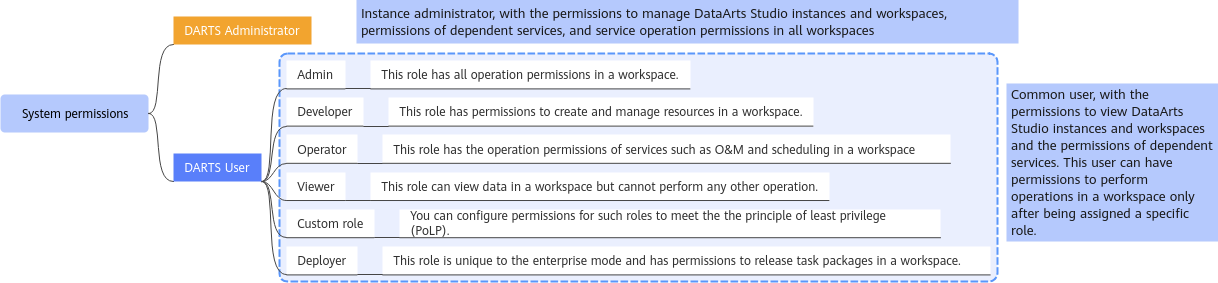
Figure 1 Permission system¶
Role | Description | Type |
|---|---|---|
DARTS Administrator | Instance administrator who has all management permissions on a DataArts Studio instance and its workspaces, permissions of dependent services, and service operation permissions in all workspaces. Note Users assigned the Tenant Administrator role have all permissions for all services except IAM. In other words, users with the Tenant Administrator role can perform all operations in DataArts Studio. | System-defined role |
DARTS User | Common user who has permissions to view a DataArts Studio instance and its workspaces, and the permissions of dependent services. After assigned a role, a common user has permissions of the role to perform service operations. Workspace roles include the preset admin, developer, deployer, operator, and viewer, and other custom roles. For details about the operation permissions of each role, see Permissions.
| System-defined role |
Roles or Policies for DataArts Studio Console¶
Table 2 lists the permissions for the services on which DataArts Studio modules depend. You are advised to configure the minimum DataArts Studio-level permissions of dependent services for developers. Table 3 lists the minimum permissions for developers on the services on which DataArts Studio depends.
Note
The DARTS Administrator and DARTS User already have the administrator permissions of dependent services. If the DARTS User role is assigned to a common user or user group, the common user or user group may have more permissions of dependent services than required. To prevent this risk, you can manually delete the permissions of dependent services from the user group after assigning the DARTS User role to the user group, and then assign the minimum permissions of dependent services to the user group.
Console Function | Dependent Service | Role/Policy Required | Function |
|---|---|---|---|
Management Center | BSS | bss:coupon:view bss:renewal:update bss:discount:view bss:order:view bss:order:pay bss:order:update | Create incremental packages or DataArts Studio instances. |
KMS | kms:cmk:get kms:cmk:list kms:cmk:create kms:cmk:decrypt kms:cmk:encrypt kms:dek:create kms:dek:encrypt kms:dek:decrypt | Encrypt and decrypt data during data connection creation. | |
DWS | dws:cluster:list dws:cluster:getDetail dws:openAPICluster:getDetail | Create DWS connections. | |
MRS | mrs:cluster:get mrs:cluster:list | Create MRS connections. | |
VPC | vpc:publicIps:get vpc:publicIps:list vpc:vpcs:get vpc:subnets:get | Create MRS connections. | |
RDS | rds: rds: | Create RDS connections. | |
DataArts Migration | VPC | vpc:publicIps:get vpc:publicIps:list vpc:vpcs:get vpc:vpcs:list vpc:subnets:get vpc:securityGroups:get vpc:firewalls:list vpc:routeTables:list vpc:subNetworkInterfaces:list | Create CDM clusters or DataArts Studio instances. |
ECS | ecs:flavors:get ecs:cloudServerFlavors:get ecs:availabilityZones:list | Create CDM clusters or DataArts Studio instances. | |
CDM | cdm:cluster:create | Create CDM clusters. | |
KMS | kms:cmk:get kms:cmk:list kms:cmk:create kms:cmk:decrypt kms:cmk:encrypt kms:dek:create kms:dek:encrypt kms:dek:decrypt | Encrypt and decrypt data during data connection creation. | |
MRS | mrs:cluster:get mrs:cluster:list mrs:job:get mrs:job:list | Create MRS connections. | |
DWS | dws:cluster:list dws:cluster:getDetail dws:openAPICluster:getDetail | Create DWS connections. | |
CDM | cdm:cluster:get cdm:cluster:list cdm:link:operate cdm:job:operate | Perform operations on the CDM console. | |
CES | ces: ces: | View monitoring data in Cloud Eye. | |
CSS | css: css: | Create CSS connections. | |
CloudTable | cloudtable: cloudtable: | Create CloudTable connections. | |
RDS | rds: rds: | Create RDS connections. | |
Config | rms:resources:list | Create CDM clusters. | |
DataArts Factory | OBS | obs:object:GetObject obs:object:PutObject obs:bucket:GetBucketLocation obs:bucket:ListAllMyBuckets obs:bucket:ListBucket obs:bucket:CreateBucket | Run scripts, run jobs, and back up jobs. |
SMN | smn:topic:publish smn:topic:list | Send job notifications. | |
KMS | kms:cmk:get kms:cmk:list kms:cmk:create kms:cmk:decrypt kms:cmk:encrypt kms:dek:create kms:dek:encrypt kms:dek:decrypt | Encrypt and decrypt data during data connection creation. | |
MRS | mrs:cluster:get mrs:cluster:list mrs:job:submit mrs:job:delete mrs:job:stop mrs:sql:execute mrs:sql:cancel mrs:job:get mrs:job:list | Run the following MRS job nodes: MRS Presto SQL, MRS Spark, MRS Spark Python, MRS Flink Job, and MRS MapReduce MRS Spark SQL and MRS Hive SQL | |
DLI | dli:queue:submitJob dli:jobs:create dli:jobs:update dli:jobs:get dli:jobs:list dli:jobs:listAll | Run the following DLI job nodes: DLI SQL and DLI Spark | |
OBS | obs:object:GetObject obs:object:PutObject obs:object:DeleteObject obs:bucket:GetBucketLocation obs:bucket:ListAllMyBuckets obs:bucket:ListBucket obs:bucket:ListBucketVersions obs:bucket:CreateBucket obs:bucket:DeleteBucket | Run the following OBS job nodes: Create OBS, Delete OBS, and OBS Manager | |
DWS | dws:cluster:list dws:cluster:getDetail dws:openAPICluster:getDetail | Create DWS connections. | |
CDM | cdm:cluster:get cdm:cluster:list cdm:job:operate | Run the Agent-related scripts and jobs required by data connections and run CDM jobs: RDS SQL, DWS SQL, Hive SQL, SPARK SQL, Shell, and Python | |
CES | ces:metricData:list | Query the CPU usage of the DLI queue on the Overview page. | |
GES | ges:graph:access ges:graph:operate ges:graph:list ges:graph:getDetail ges:metadata:create ges:metadata:operate ges:metadata:delete ges:metadata:list ges:metadata:getDetail ges:jobs:list ges:jobs:getDetail | Run the Import GES job node. | |
ECS | ecs:servers:list ecs:servers:get ecs:servers:stop ecs:servers:start ecs:cloudServers:list | Run the Open/Close Resource job node and create host connections. | |
DLI | dli:queue:submitJob dli:queue:cancelJob dli:group:useGroup dli:group:getGroup dli:group:updateGroup dli:group:deleteGroup dli:group:listAllGroup dli:database:createDatabase dli:database:dropDatabase dli:database:displayDatabase dli:database:displayAllDatabases dli:database:explain dli:database:createView dli:database:createTable dli:database:displayAllTables dli:database:createFunction dli:database:describeFunction dli:database:showFunctions dli:database:dropFunction dli:table:select dli:table:update dli:table:delete dli:table:dropTable dli:table:describeTable dli:table:showCreateTable dli:table:showPartitions dli:table:showSegments dli:table:showTableProperties dli:table:insertOverwriteTable dli:table:insertIntoTable dli:table:compaction dli:table:truncateTable dli:table:alterView dli:table:alterTableRename dli:table:alterTableAddColumns dli:table:alterTableDropColumns dli:table:alterTableChangeColumn dli:table:alterTableSetLocation dli:table:alterTableAddPartition dli:table:alterTableRenamePartition dli:table:alterTableSetProperties dli:table:alterTableRecoverPartition dli:table:alterTableDropPartition dli:column:select dli:jobs:create dli:jobs:delete dli:jobs:start dli:jobs:stop dli:jobs:update dli:jobs:export dli:jobs:get dli:jobs:list dli:jobs:listAll dli:resource:useResource dli:resource:updateResource dli:resource:deleteResource dli:resource:getResource dli:resource:listAllResource dli:variable:update dli:variable:delete | Run DLI jobs/scripts. | |
IAM | iam:agencies:listAgencies | Obtain job agencies. | |
DIS | DIS Operator DIS User | Run the following DIS job nodes: DIS Stream, DIS Dump, and DIS Client | |
SWR | SWR Admin | The image read permission in SWR is required only when a custom image is selected for a DLI Spark node of a job in DataArts Factory. You are advised to add the read permission of the image by referring to . You are not advised to directly assign the SWR Admin system role to users because this may result in excessive permissions. | |
DataArts Catalog | OBS | obs:object:GetObject obs:bucket:GetBucketStorage obs:bucket:GetBucketLocation obs:bucket:ListAllMyBuckets obs:bucket:ListBucket | Collect OBS metadata. |
DIS | dis:streams:list dis:transferTasks:list | Collect DIS metadata. | |
CSS | css:cluster:list | Collect CSS metadata. | |
GES | ges:graph:list ges:graph:getDetail ges:metadata:list ges:metadata:getDetail | Collect GES metadata. | |
DLI | dli:database:displayDatabase dli:database:displayAllDatabases dli:table:select dli:table:describeTable dli:table:showPartitions dli:table:showTableProperties dli:jobs:create dli:jobs:get | Collect DLI metadata and analyze data in summary. | |
CDM | cdm:cluster:list | Collect CSS metadata. | |
DataArts Quality | SMN | smn:topic:publish smn:topic:list | Configure job notifications. |
OBS | obs:object:GetObject obs:object:PutObject obs:bucket:GetBucketLocation obs:bucket:ListAllMyBuckets obs:bucket:ListBucket obs:bucket:CreateBucket | Export quality reports. | |
MRS | mrs:job:submit mrs:sql:execute mrs:sql:cancel mrs:job:get | Run MRS quality jobs. | |
DLI | dli:queue:submitJob dli:jobs:get dli:jobs:listAll | Run DLI quality jobs. | |
DataArts Security | DLI | dli:queue:submitJob dli:queue:cancelJob dli:database:displayDatabase dli:database:displayAllDatabases dli:database:displayAllTables dli:table:describeTable dli:jobs:create dli:jobs:stop dli:jobs:get dli:resource:deleteResource dli:resource:getResource dli:resource:listAllResource | Manage DLI permissions. |
DWS | dws:cluster:list dws:cluster:getDetail dws:openAPICluster:getDetail | Manage DWS permissions. | |
MRS | mrs:cluster:list mrs:job:submit mrs:job:stop | Manage MRS permissions. | |
KMS | kms:cmk:list kms:cmk:encrypt kms:cmk:decrypt | Encrypt and decrypt data using KMS. | |
CDM | Any CDM permission, for example, cdm:cluster:get | Manage DWS and MRS permissions. |
Permission Type | Role/Policy-based permissions-system role | Role/Policy-based permissions-custom policy | Role/Policy-based permissions-custom policy |
Mandatory | Mandatory | Mandatory | Mandatory |
Permission |
| DataArtsStudio_PermissionsOfDependentServices_global: custom policy for a global dependent cloud service {
"Version": "1.1",
"Statement": [
{
"Effect": "Allow",
"Action": [
"obs:object:GetObject",
"obs:object:PutObject",
"obs:object:DeleteObject",
"obs:bucket:GetBucketStorage",
"obs:bucket:GetBucketLocation",
"obs:bucket:ListAllMyBuckets",
"obs:bucket:ListBucket",
"obs:bucket:ListBucketVersions",
"obs:bucket:CreateBucket",
"obs:bucket:DeleteBucket",
"rms:resources:list",
"iam:agencies:listAgencies"
]
}
]
}
| DataArtsStudio_PermissionsOfDependentServices_region: custom policy for a regional dependent cloud service {
"Version": "1.1",
"Statement": [
{
"Effect": "Allow",
"Action": [
"cdm:cluster:get",
"cdm:cluster:list",
"cdm:cluster:create",
"cdm:link:operate",
"cdm:job:operate",
"ces:*:get",
"ces:*:list",
"cloudtable:*:get",
"cloudtable:*:list",
"css:*:get",
"css:*:list",
"dis:streams:list",
"dis:transferTasks:list",
"dli:queue:submitJob",
"dli:queue:cancelJob",
"dli:table:insertOverwriteTable",
"dli:table:insertIntoTable",
"dli:table:alterView",
"dli:table:alterTableRename",
"dli:table:compaction",
"dli:table:truncateTable",
"dli:table:alterTableDropColumns",
"dli:table:alterTableSetProperties",
"dli:table:alterTableChangeColumn",
"dli:table:showSegments",
"dli:table:alterTableRecoverPartition",
"dli:table:dropTable",
"dli:table:update",
"dli:table:alterTableDropPartition",
"dli:table:alterTableAddPartition",
"dli:table:alterTableAddColumns",
"dli:table:alterTableRenamePartition",
"dli:table:delete",
"dli:table:alterTableSetLocation",
"dli:table:describeTable",
"dli:table:showPartitions",
"dli:table:showCreateTable",
"dli:table:showTableProperties",
"dli:table:select",
"dli:resource:updateResource",
"dli:resource:useResource",
"dli:resource:getResource",
"dli:resource:listAllResource",
"dli:resource:deleteResource",
"dli:database:explain",
"dli:database:createDatabase",
"dli:database:dropFunction",
"dli:database:createFunction",
"dli:database:displayAllDatabases",
"dli:database:displayAllTables",
"dli:database:displayDatabase",
"dli:database:describeFunction",
"dli:database:createView",
"dli:database:createTable",
"dli:database:showFunctions",
"dli:database:dropDatabase",
"dli:group:useGroup",
"dli:group:updateGroup",
"dli:group:listAllGroup",
"dli:group:getGroup",
"dli:group:deleteGroup",
"dli:column:select",
"dli:jobs:start",
"dli:jobs:export",
"dli:jobs:update",
"dli:jobs:list",
"dli:jobs:listAll",
"dli:jobs:get",
"dli:jobs:delete",
"dli:jobs:create",
"dli:jobs:stop",
"dli:variable:update",
"dli:variable:delete",
"dws:cluster:list",
"dws:cluster:getDetail",
"dws:openAPICluster:getDetail",
"ecs:servers:get",
"ecs:servers:list",
"ecs:servers:stop",
"ecs:servers:start",
"ecs:flavors:get",
"ecs:cloudServerFlavors:get",
"ecs:cloudServers:list",
"ecs:availabilityZones:list",
"ges:graph:access",
"ges:metadata:create",
"ges:jobs:list",
"ges:graph:operate",
"ges:jobs:getDetail",
"ges:graph:getDetail",
"ges:graph:list",
"ges:metadata:list",
"ges:metadata:getDetail",
"ges:metadata:delete",
"ges:metadata:operate",
"kms:cmk:get",
"kms:cmk:list",
"kms:cmk:create",
"kms:cmk:decrypt",
"kms:cmk:encrypt",
"kms:dek:create",
"kms:dek:encrypt",
"kms:dek:decrypt",
"mrs:cluster:get",
"mrs:cluster:list",
"mrs:job:get",
"mrs:job:list",
"mrs:job:submit",
"mrs:job:stop",
"mrs:job:delete",
"mrs:sql:execute",
"mrs:sql:cancel",
"rds:*:get",
"rds:*:list",
"smn:topic:publish",
"smn:topic:list",
"vpc:publicIps:list",
"vpc:publicIps:get",
"vpc:vpcs:get",
"vpc:vpcs:list",
"vpc:subnets:get",
"vpc:securityGroups:get",
"vpc:firewalls:list",
"vpc:routeTables:list",
"vpc:subNetworkInterfaces:list"
]
}
]
}
|