Authenticating JWT Requests on the Ingress Gateway Using ASM¶
This section describes how to authenticate JWT requests on the ingress gateway using ASM to ensure that users access services through the ingress gateway with a reliable access token.
Preparations¶
A service mesh of version 1.15 or 1.18 has been created.
The httpbin service that passes the diagnosis exists in the mesh. The image is httpbin, the port protocol is HTTP, and the port number is 80.
An accessible gateway has been created for the httpbin service in the mesh.
Creating JWT Authentication¶
Create a JWK.
Visit JWT tool website, set Algorithm to RS512, and obtain the public key (PUBLIC KEY).
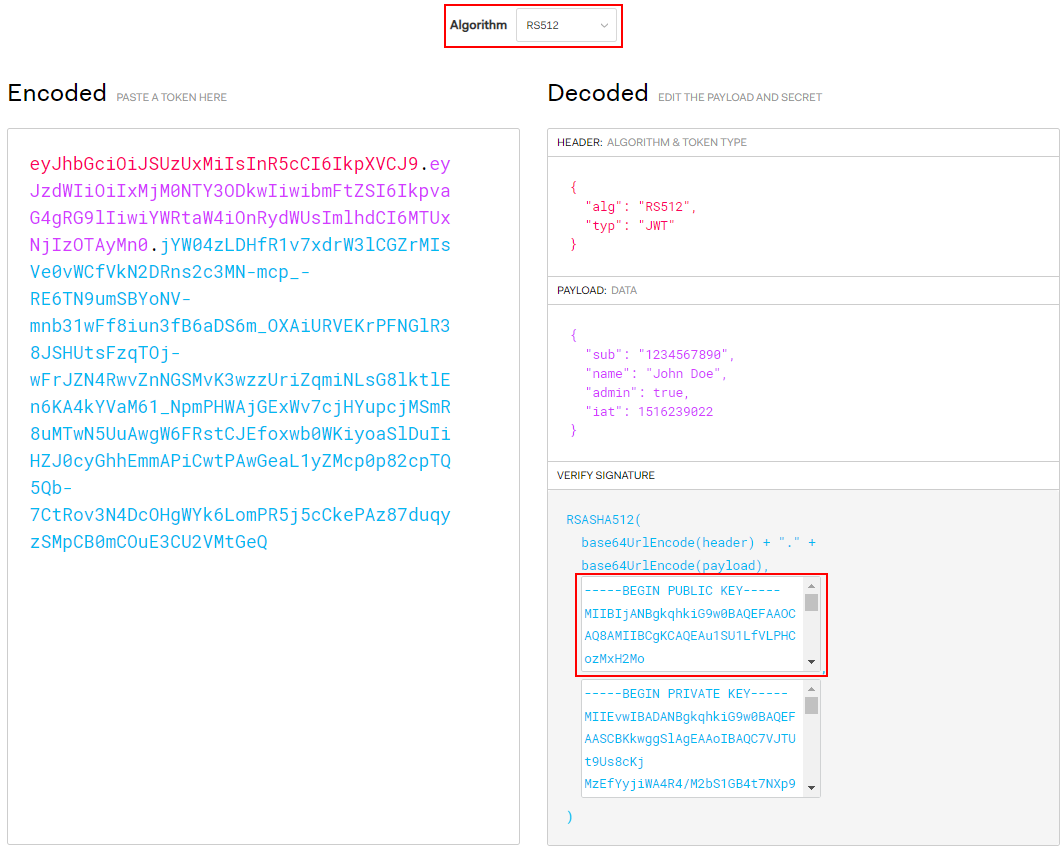
Figure 1 Generating a public key¶
Select PEM-to-JWK (RSA Only) in the JWK to PEM Convertor online tool, enter the public key obtained in the previous step, and click submit to convert the public key into a JWK.
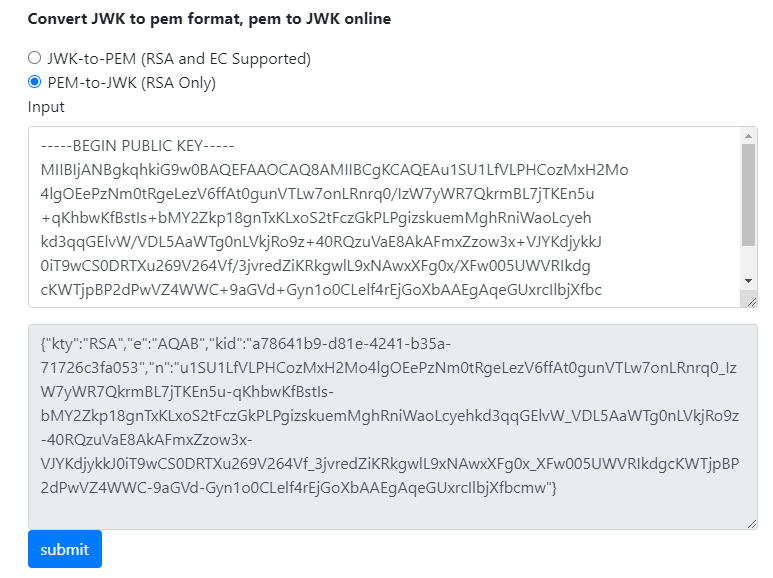
Figure 2 Converting the public key to a JWK¶
{"kty":"RSA","e":"AQAB","kid":"a78641b9-d81e-4241-b35a-71726c3fa053","n":"u1SU1LfVLPHCozMxH2Mo4lgOEePzNm0tRgeLezV6ffAt0gunVTLw7onLRnrq0_IzW7yWR7QkrmBL7jTKEn5u-qKhbwKfBstIs-bMY2Zkp18gnTxKLxoS2tFczGkPLPgizskuemMghRniWaoLcyehkd3qqGElvW_VDL5AaWTg0nLVkjRo9z-40RQzuVaE8AkAFmxZzow3x-VJYKdjykkJ0iT9wCS0DRTXu269V264Vf_3jvredZiKRkgwlL9xNAwxXFg0x_XFw005UWVRIkdgcKWTjpBP2dPwVZ4WWC-9aGVd-Gyn1o0CLelf4rEjGoXbAAEgAqeGUxrcIlbjXfbcmw"}
Create JWT authentication.
Log in to the ASM console and click the name of the target service mesh to go to its details page.
In the navigation pane, choose Service Management. In the upper right corner of the list, select the namespace that your services belong to.
Locate the httpbin service and click Security in the Operation column. In the window that slides out from the right, click JWT Authentication and then Configure now. In the displayed dialog box, set the following parameters:
Issuer: issuer of the JWT. Set this parameter to test.
Audience: JWT audiences who use the JWT token to access the target service. Set this parameter to ASM.
JWKS: JWT information. Set this parameter to {"keys": [JWK created in :ref:`1 <asm_01_0097__li116016915174>`]}. For example, if the JWK created in 1 is {"kty":"RSA","e":"AQAB","kid":"a78641b9-d81e-4241-b35a-71726c3**"}**, the value of JWKS is {"keys": [{"kty":"RSA","e":"AQAB","kid":"a78641b9-d81e-4241-b35a-71726c3**"}]}**.
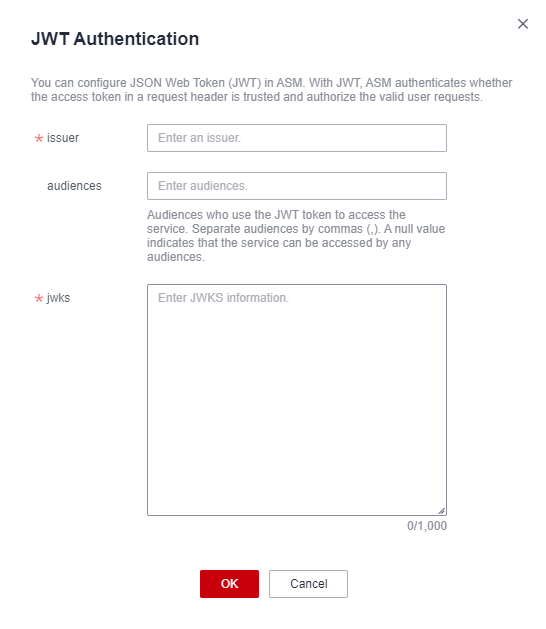
Figure 3 Creating JWT authentication¶
Click OK.
Checking Whether JWT Authentication Takes Effect¶
Use JWT tool to encode the JWT request information into a JWT token.
Enter the following JWT request information in the Decoded area. The automatically converted JWT token is displayed in the Encode area.
HEADER: Set alg to RS512, enter kid in the JWK created in 1, and set typ to JWT.
PAYLOAD: Set iss to test and aud to ASM. Ensure that the values are the same as the issuer and token audience configured in 2.
VERIFY SIGNATURE: The value must be the same as the public key in 1.a.
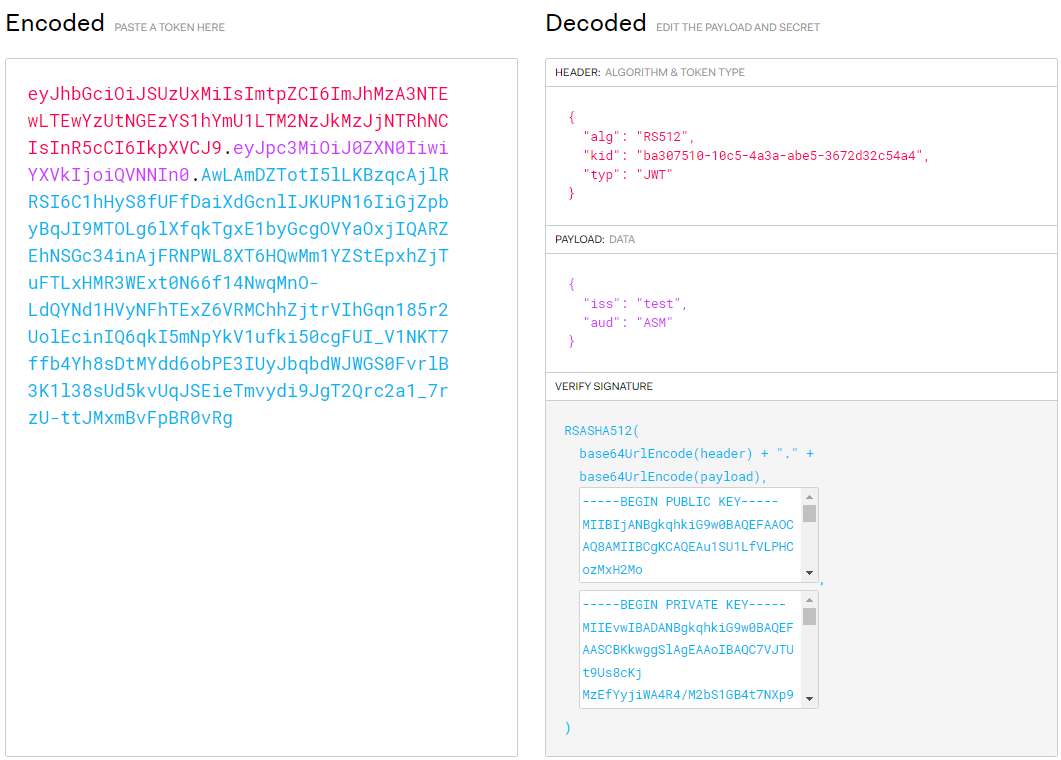
Figure 4 Creating a JWT token¶
Access the httpbin service through the ingress gateway.
Run the following commands to access the service with the JWT token created in 1:
TOKEN=JWT token created by the :ref:`1 <asm_01_0097__li174941250183818>`.
curl -I -H "Authorization: Bearer $TOKEN" http:// {External access address of the httpbin service}/
Expected outputs:
HTTP/1.1 200 OK server: istio-envoy date: Wed, 21 Sep 2022 03:11:48 GMT
Run the following command to access the service with an invalid JWT token:
curl -I -H "Authorization: Bearer invalidToken" http:// {External access address of the httpbin service}/
Expected outputs:
HTTP/1.1 401 Unauthorized www-authenticate: Bearer realm="http://***.***.***.***:***/", error="invalid_token" content-length: 145 content-type: text/plain date: Wed, 21 Sep 2022 03:12:54 GMT server: istio-envoy x-envoy-upstream-service-time: 19
Modify the JWT authentication created in 2, leave the aud empty (indicating that the service can be accessed by any services), and run the following command to access the service with the JWT token created in 1:
curl -I -H "Authorization: Bearer $TOKEN" http:// {External access address of the httpbin service}/
Expected outputs:
HTTP/1.1 200 OK server: istio-envoy date: Wed, 21 Sep 2022 03:20:07 GMT
Run the following command to access the service without the JWT token:
curl -I http:// {External access address of the httpbin service}/
Expected outputs:
HTTP/1.1 403 Forbidden content-length: 85 content-type: text/plain date: Wed, 21 Sep 2022 03:29:31 GMT server: istio-envoy x-envoy-upstream-service-time: 6
According to the preceding outputs, the request with the correct JWT token can access the service, and the request with an incorrect JWT token or without a JWT token cannot access the service. This means the request identity authentication takes effect.